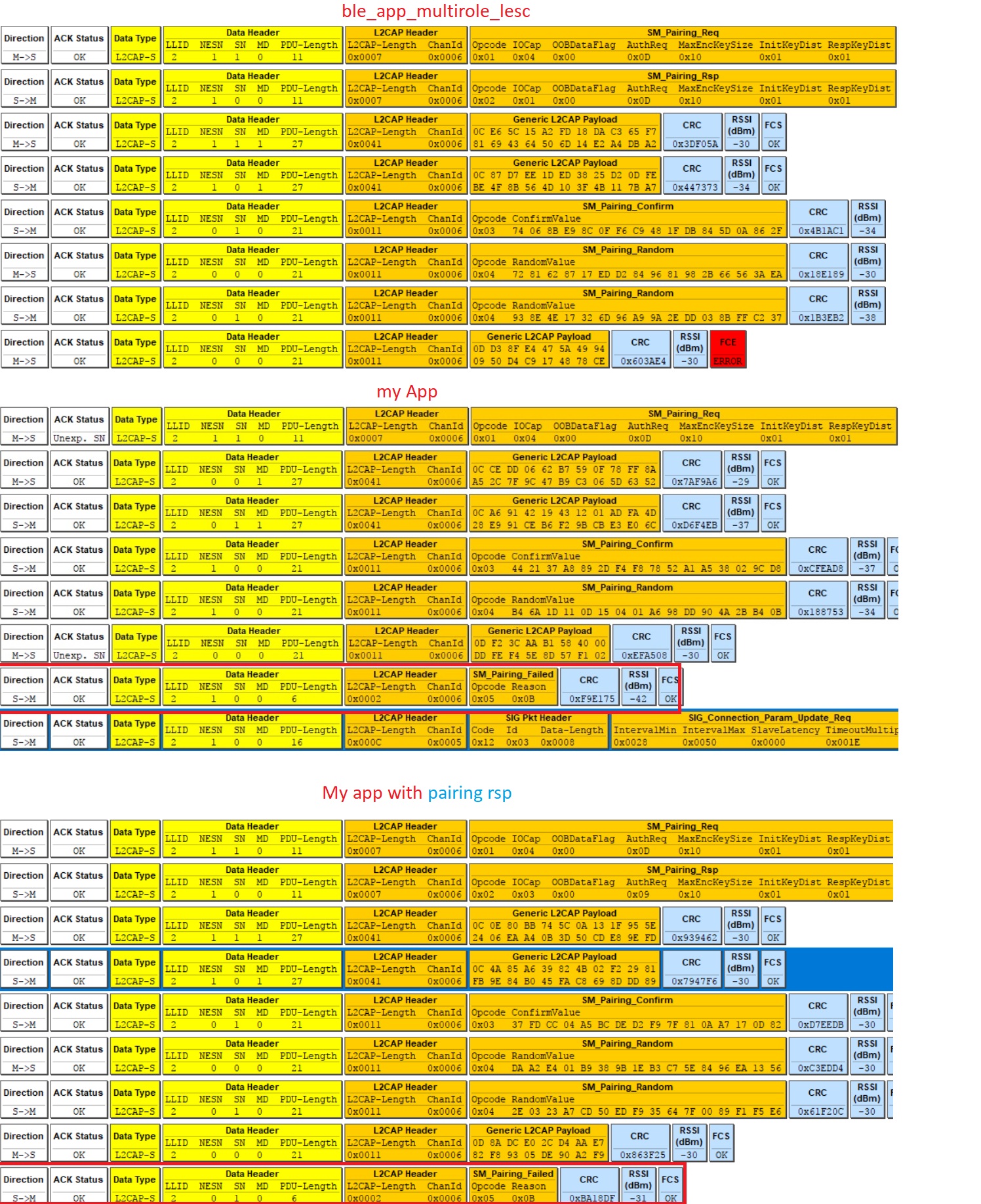
Hi all,
I have tried to mimic the LESC multi role example to my own app, but I dint have luck to pair it using LESC, MITM, and perform bonding and I received a SM_pairing_faill reason 0x0b; screen capture below:
nRF connect PC
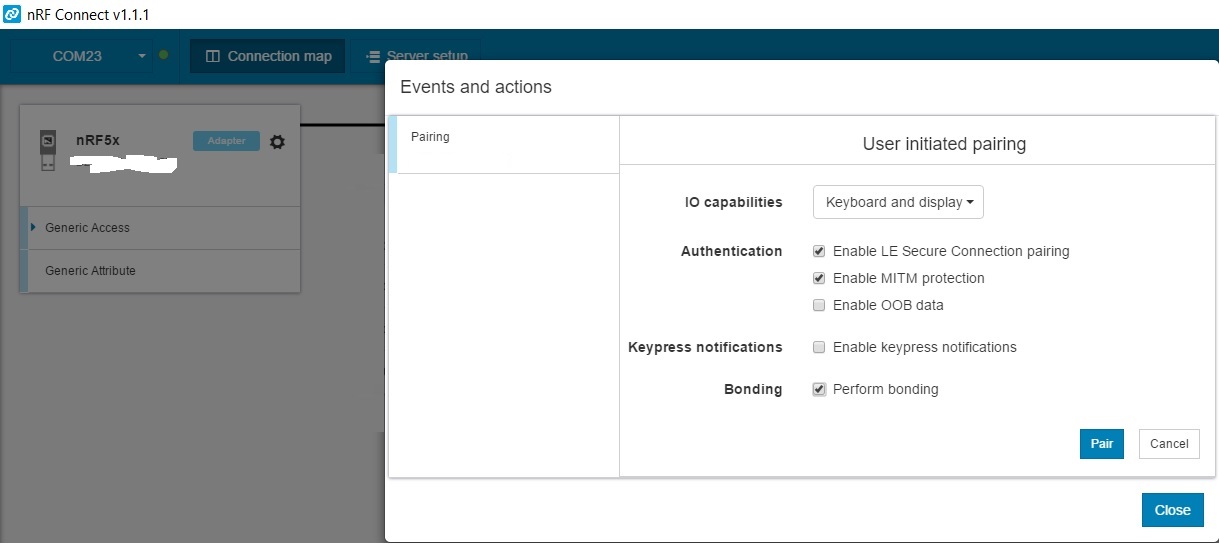
nRF connect PC failing to pair
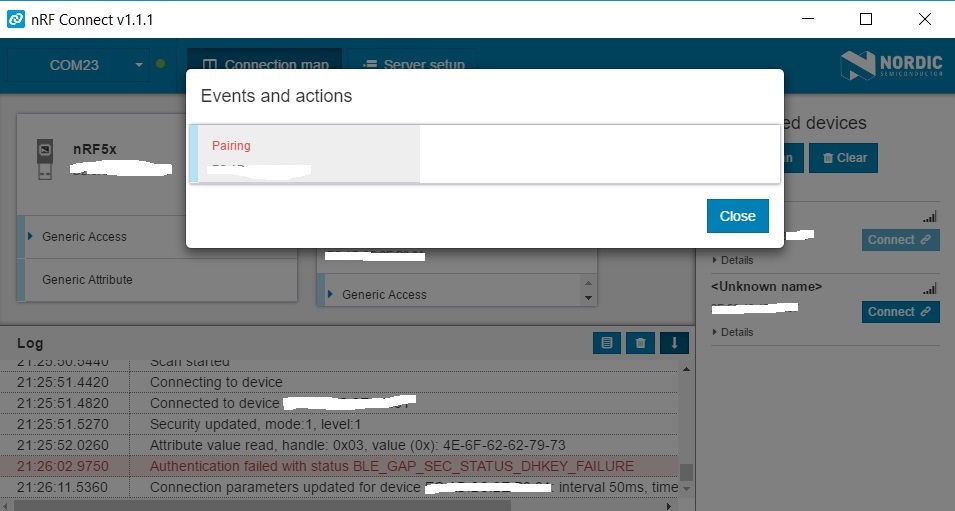
sniffer capture
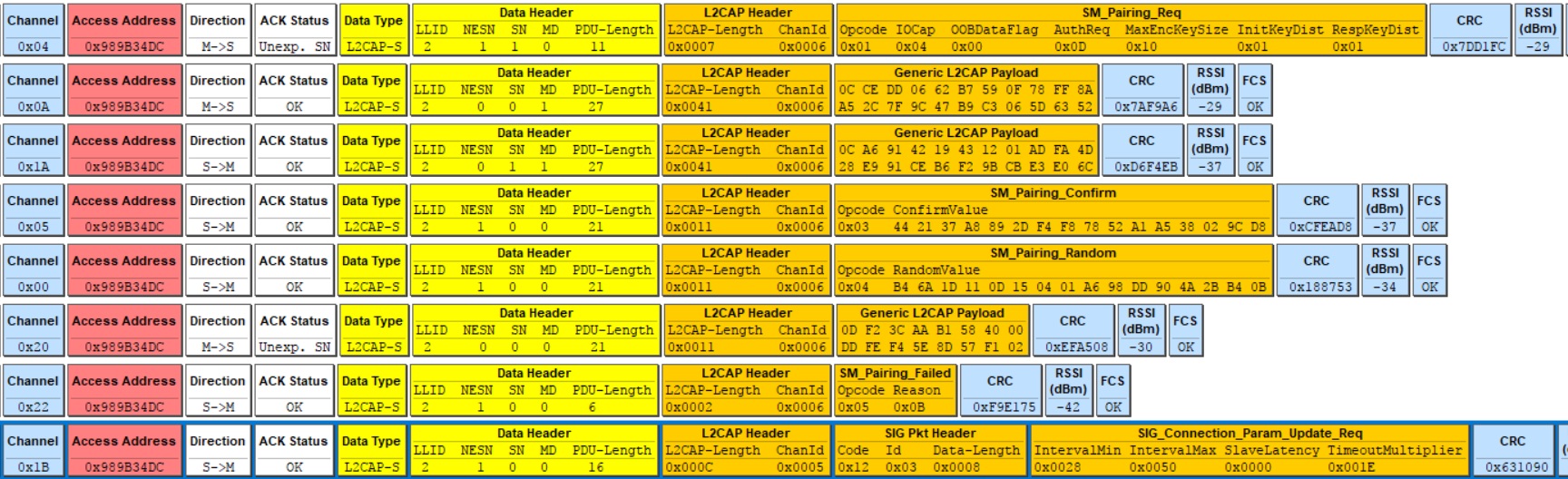
details: Peripheral running on my peripheral device nRF52 with SDK13. Central using a nRF51 using PC nRF connect firmware.
My device does not have any Input, I am trying to perform LESC with just work
sec_params.bond = true;
sec_params.mitm = false;
sec_params.lesc = true;
sec_params.keypress = false;
sec_params.io_caps = false;
sec_params.oob = false;
sec_params.min_key_size = 7;
sec_params.max_key_size = 16;
sec_params.kdist_own.enc = 1;
sec_params.kdist_own.id = 1;
sec_params.kdist_peer.enc = 1;
sec_params.kdist_peer.id = 1;
I tried use nRF connect (pc version) with the multi role example and it works with no issue, and I am pretty sure it is equal on my app (same settings), but I am stuck in the SM_paring_failed.