-
Using SDK 7.2 and S110 7.1
-
IDE : IAR 7.1
-
Board : PCA10001 (Revision 2 MCU)
Hi, regardless of the example, when I add some codes of my own,
there are some cases when the firmware falls into HardFault_Handler
(or other Handlers such as BusFault_Handler).
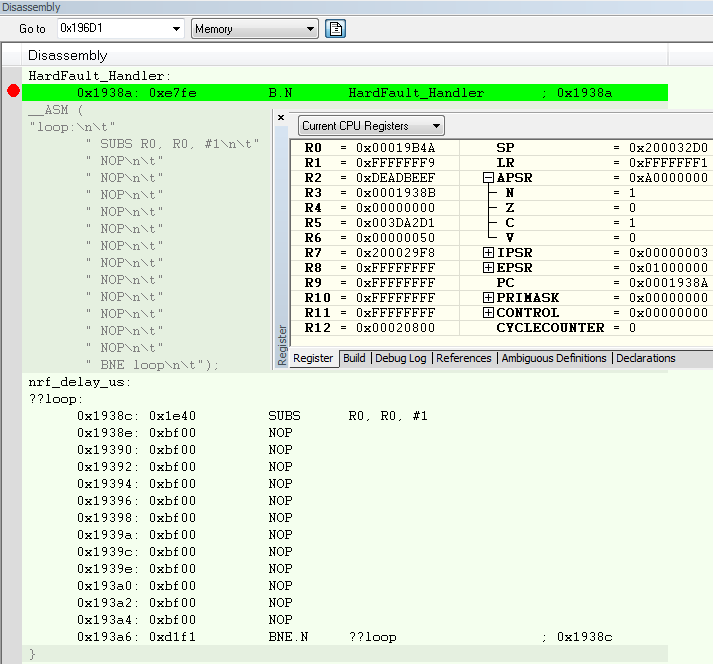
Comparing to the situation such as SDK function returns error code,
it is easy for developers to tell what code is the problem.
Whereas when the code falls into HardFault_Handler,
is there a way to identify what cased this problem?
Added : 23, July, 2015
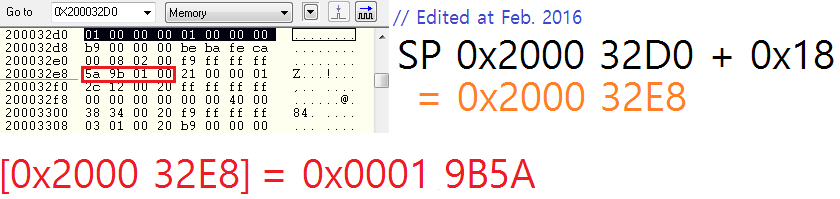
One more thing, do I have to consider the endian?
Since nRF51822-QFAA is based on little-endian,
is [0X2000 32D0] = 0x0001 0000 or 0x0100 0000?
If it's 0x0001 0000 (code instruction at 0x0001 0018), then this means the SoftDevice has caused a HardFault?
In my case, as mentioned above, I use SoftDevice S110 7.1 and SDK 7.2.
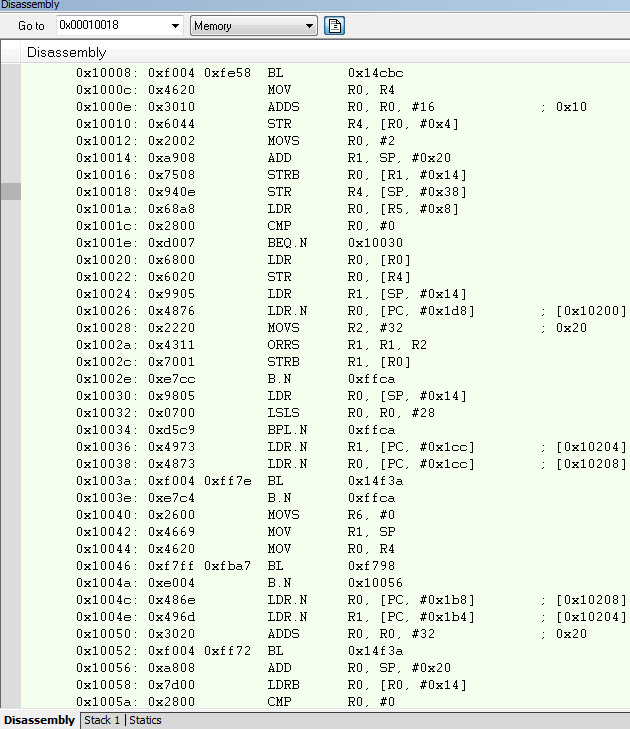
This is the Dissembly window.
(If showing the instructions of the SoftDevice is illegal, please notice me and I will edit this part.)
Also, this is a part of the .map file.
Section Kind Address Size Object
------- ---- ------- ---- ------
"A1": 0xc0
.intvec ro code 0x00016000 0xc0 iar_startup_nrf51.o [1]
- 0x000160c0 0xc0
"P1": 0x7c00
.text ro code 0x000160c0 0xf14 device_manager_peripheral.o [1]
.text ro code 0x00016fd4 0x28 memcmp.o [4]
.text ro code 0x00016ffc 0x64 ABImemset.o [4]
.text ro code 0x00017060 0x5c ABImemcpy.o [4]
.text ro code 0x000170bc 0x8cc pstorage.o [1]
.text ro code 0x00017988 0xe0 I32DivModFast.o [4]
.text ro code 0x00017a68 0x2 IntDivZer.o [4]
.text ro code 0x00017a6a 0x2a zero_init3.o [4]
Added again : 23, July, 2015
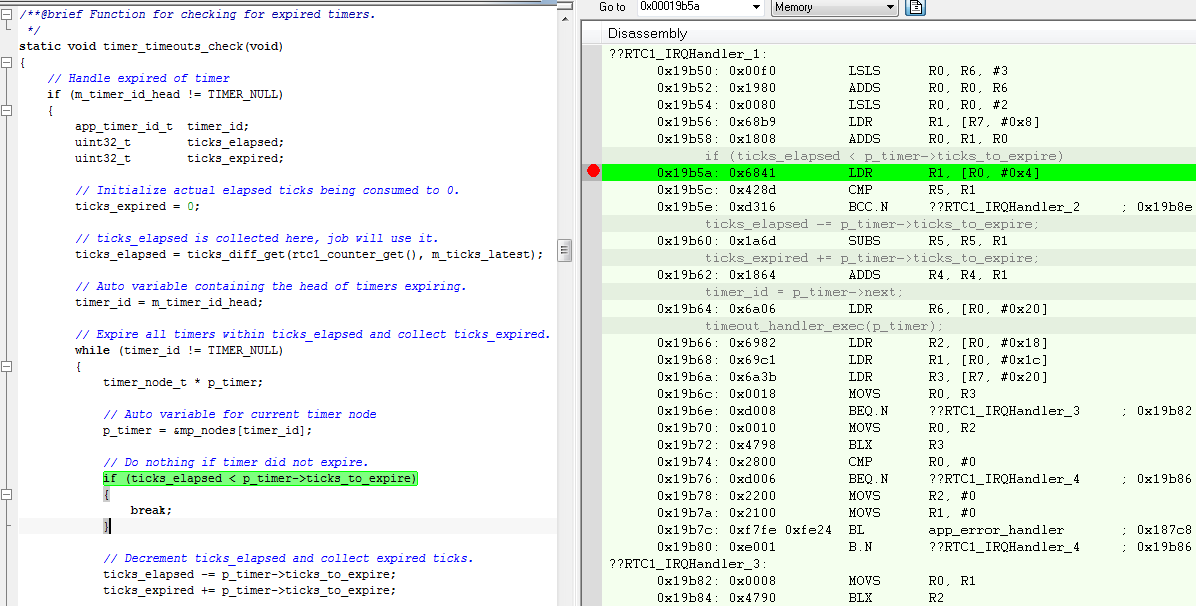
@RK : At 0x00019b5a, it was LDR command.
-Regards

