Hi,
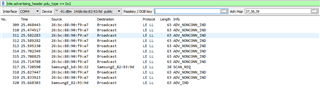
I'm trying to capture Mesh packets using nRF Sniffer 2.0.0 and nRF52 DK while running the Light switch demo, but so far I haven't been able to capture any packet that I could identify as belonging to the Mesh network.
I do capture a lot of other packets like SCAN_REQ or ADV_IND, even with the Mesh nodes off.
I followed the instructions on nRF Sniffer User Guide v2.1, and I'm using Wireshark 2.4.6, Python 2.7.14 and pyserial 3.4. My Adv Hop settings are as default: 37,38,39.
Besides not being able to capture Mesh packets, I also often get the following error message: "Unable to send control message: Invalid argument." usually followed by some error starting with "Error by extcap pipe: Exception in thread Thread-3:"
I'm also using J-Link V6.30.
I fully followed the User Guide, so I really don't know why I can't see any Mesh packets.
Additionally, using btle.advertising_header.pdu_type == 0x2 filter in wireshark doesn't help either, I see ADV_NONCONN_IND packets but from one source address only, instead of 3 (1 client and 2 servers).
What could be the problem?