Hi,
We are developing a wireless sensor for research purpose using NRF52. I was always develop under Bluetooth 5.0 environments. The phone i am always using is Xiaomi MI 6, which supports Bluetooth 5. We are using data length extension for higher data rate.
Recently, we want to support older 4.1 and 4.0 device. I tried a few time but failed.
Hardly i set up the NRF Sniffer with Wireshark. Here are the logs.
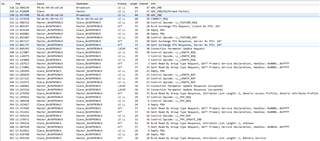
This log is from Xiaomi MI 6 (Bluetooth 5). In this log both central and peripherals are working fine.
When i tried with Nexus 6 (Bluetooth 4.1). The connection cannot be established. Peripheral disconnects after timeout.
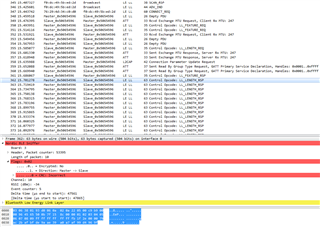
Could you give me some advice of what might cause this problem?
Environment: SDK 14.1, SD132 V5, NRF52832
My code are based on nus example but however totally revised to implement an RTOS. And i also implement some structures from NRF52 Thingy (crossing SDK version might have some problem).
I think one of the problem might be some BLE event didn't handle properly.
Both logs above are in here
/cfs-file/__key/support-attachments/beef5d1b77644c448dabff31668f3a47-e4ead8af96f34d2cafc33581beabc35b/nexus-6.pcapng/cfs-file/__key/support-attachments/beef5d1b77644c448dabff31668f3a47-e4ead8af96f34d2cafc33581beabc35b/xiaomi-mi6.pcapng
Thanks for your time,
Jianjia


