I have a smartwatch, smartphone, and tablet.
I went to some place without any other bluetooth devices, my devices are able to scan and pair with each other. But nRF-51 not able to see any of those devices in the Wireshark Device drop-down. It is empty. And then I went back to the lab and I'm able to see all other Bluetooth devices with nRF-51.
I'm using the OS X runs the nRF Sniffer software v2. Wireshark V2.4.2. SEGGER J-Link v6.16c.
I tried all the common sniffing actions in "nRF_Sniffer_User_Guide_v2.1.pdf", I just cannot find my devices in Devices drop-down list.
I have tried those actions:
1. Before the devices pair, I turn on the Bluetooth scanning mode in each device, my Wireshark Devices drop-down list is empty.
2. During the devices paring, my Wireshark Devices drop-down list still empty.
3. After the devices paired, my Wireshark Devices drop-down list still empty.
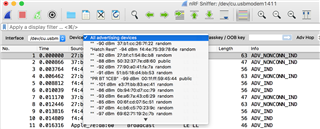
This screenshot shows that I am able to see other devices besides my watch, phone, and tablet.
I saw a thread from Stack overflow mentions about the Bluetooth LE peripheral mode. I'm not sure if this causes my problem here.


