I'm currently working an nRF52 using SDK 14.1 and Softdevice 5.0.0
We're having a problem where the microcontroller is crashing after a few days for seemingly no reason. We have bluetooth services running, and timers performing tasks (such as reading from an accelerometer or an ADC) in the background. If we leave our device powered on but unconnected to other devices (so it's only advertising) we see this error after a few days and it crashes. It's quite difficult to catch the bug because we need to keep it connected to a debugger for several days but here are some screenshots from backtracing
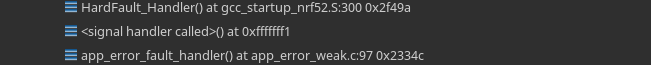
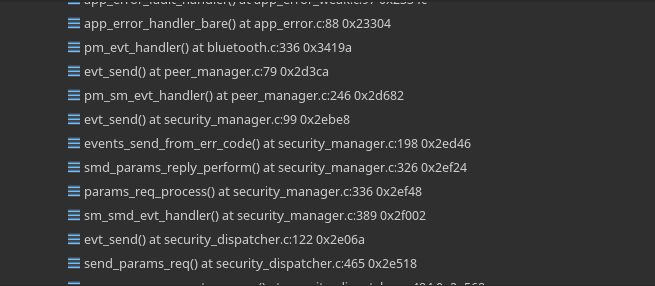
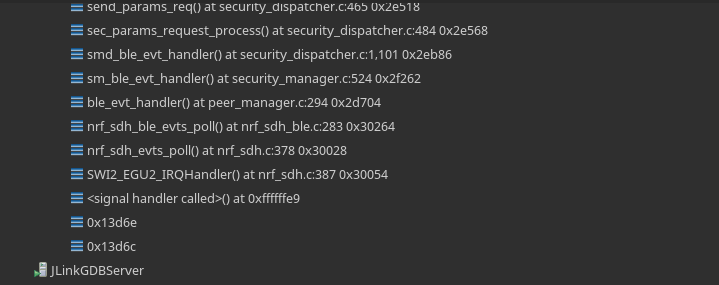
Going through the code manually it looks like there is a BLE_GAP_EVT_PARAMS_REQUEST and this is passed onto the security dispatch module who receives a PM_EVT_CONN_SEC_PARAMS_REQ and from the smd_params_reply function, error code 6 (PM_EVT_ERROR_UNEXPECTED) is received. It looks like this can be generated by a variety of functions within smd_params_reply however so this is where I've gotten a bit lost. Short of just adding breakpoints in each of these function to check their return codes, I'm not sure where to go from here. I also thought it might be my bluetooth configuration so here is a screenshot for that:
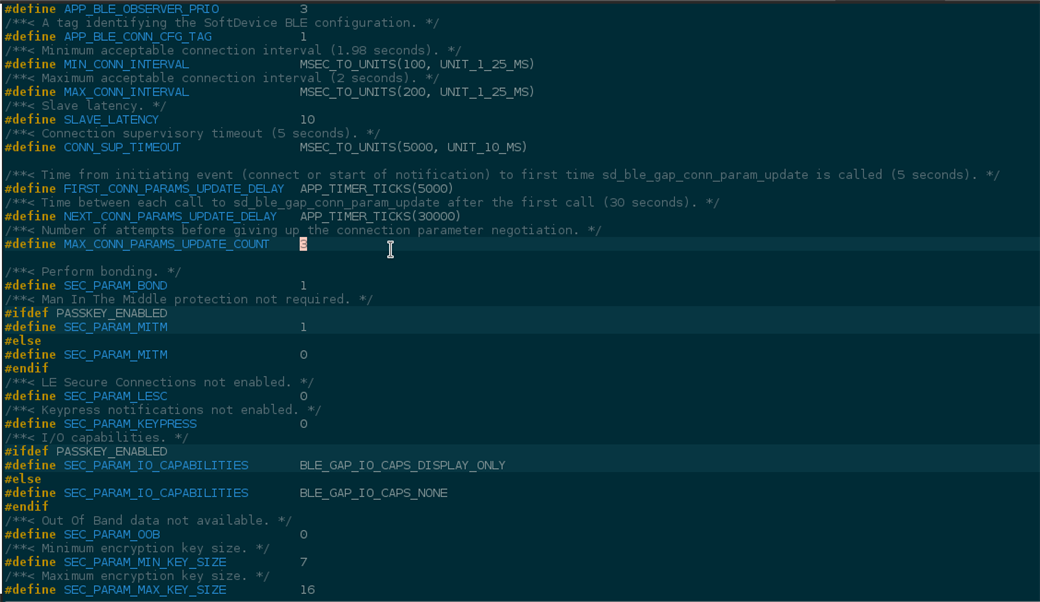
I've looked around at other people encountering this error and their problems don't seem to be linked to mine so any help would be appreciated.


