Hi,
I am trying to test an application running on the nRF52840 using your nRF Sniffer (actual version 2.0.0.2.beta).
My application should be able to request a change of the Bluetooth packet data length (DLE feature available since BLE 4.2) and it does so by calling the function nrf_ble_gatt_data_length_set .
It seems that this works. I use a packet data length of 71 bytes and ATT_MTU = 67 bytes and data are received correctly by the peer.
However I have a problem with the nRF Sniffer:
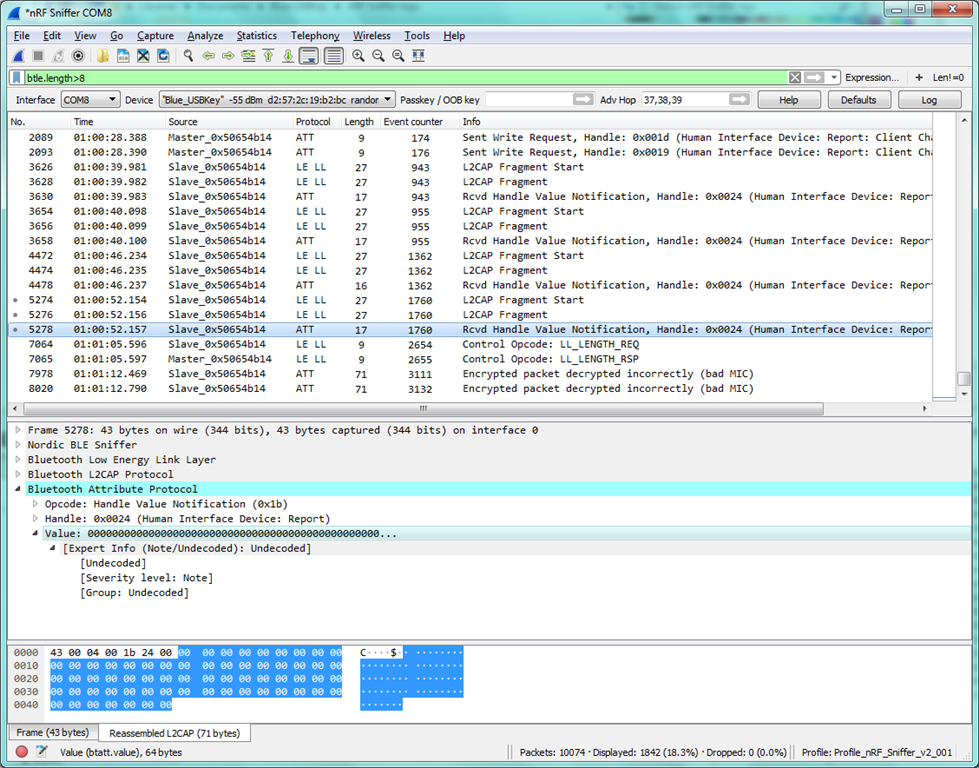
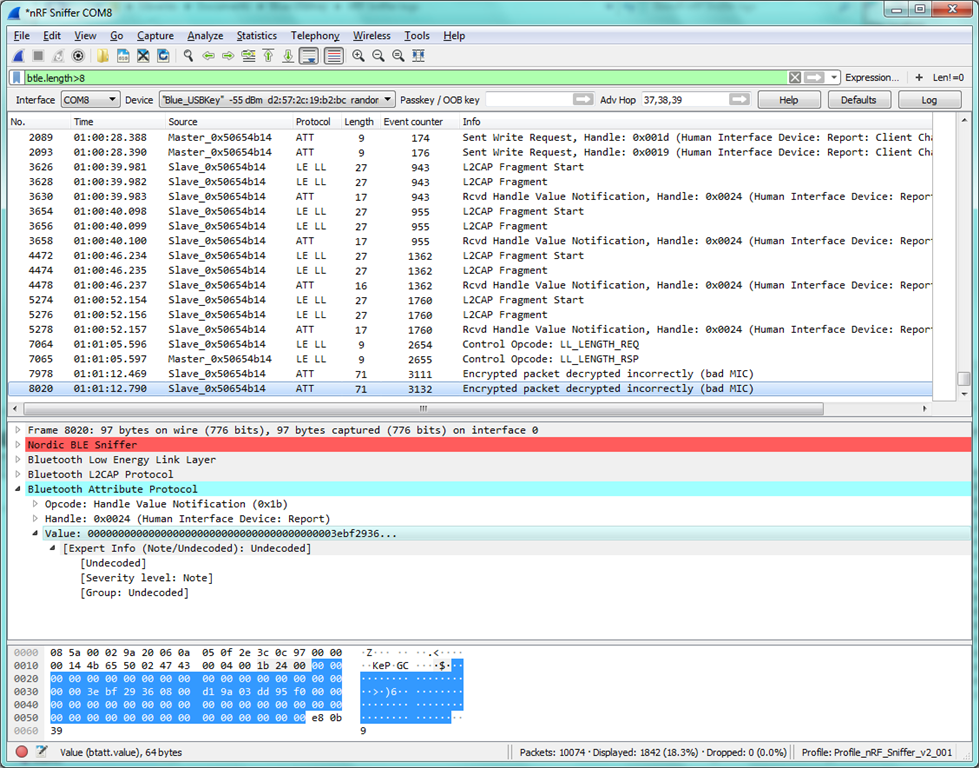
After changing the packet data length on an existing connection (sniffed correctly so far with the default packet data length of 27 bytes), the nRF Sniffer looses track of the encryption as soon as a packet is sent with a data length larger than the default 27 bytes. Starting from this moment, all subsequent packets are flagged with the following error message:
"Encrypted packet decrypted incorrectly (bad MIC)"
even if their packet data length is smaller than 27 bytes.
Can you confirm that this is a known bug or a missing feature of the nRF Sniffer?
In the latter case, I would urge you to document this limitation in the nRF Sniffer documentation!
Is a fix or feature implementation planned?
Thank you very much.