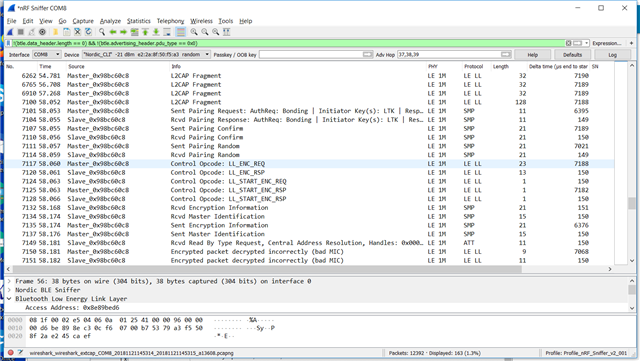
I am a newbie with nRF Sniffer, which I have installed on one PCA10040 board. I am sniffing communications between a Samsung phone running nRF Connect and a second PCA10040 running the glucose sample app.
I believe I am following the instructions in the User Guide section 5.5: when the glucose app prints the 6-digit passkey I enter this into Wireshark and type enter, then I enter it into the phone. The phone and peripheral then bond and work, but Wireshark starts printing "Encrypted packet decrypted incorrectly (Bad MIC)" . When I click on Log I see this:
INFO: Setting Passkey: 691295
INFO: Sent key value to sniffer: [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 10, 140, 95]
A screenshot is here:
/resized-image/__size/640x480/__key/support-attachments/beef5d1b77644c448dabff31668f3a47-e588f28969f94ee0a39b08c9e8afde0d/Screenshot-2018_2D00_11_2D00_19-10.57.32.png
Q1: Are my results expected? What should I do differently?
Q2: Assuming I am able to get beyond this problem, is it possible to sniff subsequent connections? The Central and Peripheral will be bonded and the peripheral will not print a passkey. Can nRF Sniffer decrypt the second session based on keys it has saved?