Hi,
Are there any known Android bugs where Android should not bond, but does? I have tried searching the web without too much success.
My central device is an older Android phone, Nexus 6, running Android 7.1.1. Using nRF Connect. With that said, I was able to replicate this issue on other Android phones. The peripheral is an nRF52840.
Security parameters are being set in the peer manager handler:
static void ble_thr_pm_handler(pm_evt_t const *p_evt)
{
/* ...stuff here... */
switch(p_evt->evt_id)
{
case PM_EVT_CONN_SEC_PARAMS_REQ:
{
ble_gap_sec_params_t sec_param = {0};
ret_code_t err_code;
sec_param.bond = 0;
sec_param.mitm = 1;
sec_param.lesc = 1;
sec_param.keypress = 0;
sec_param.io_caps = BLE_GAP_IO_CAPS_DISPLAY_YESNO;
sec_param.oob = 0;
sec_param.min_key_size = 7;
sec_param.max_key_size = 16;
err_code = pm_conn_sec_params_reply(
conn_handle,
&sec_param,
p_evt->params.conn_sec_params_req.p_context
);
APP_ERROR_CHECK(err_code);
}
break;
/* ...other cases here... */
}
}
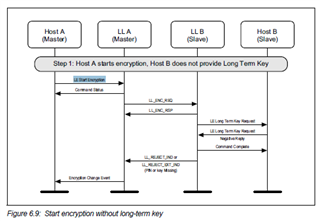
I am attaching two BLE HCI snoop logs. One, connect.log, shows the initial pairing process. Pairing is triggered by reading a characteristic (frame 26). Second file, connect-previously-paired.log, shows how Android tries to start encryption after connection is established, even though it should not (frames 30-32). nRF correctly responds with PIN or Key Missing. iOS devices seem to work okay, and do not store any bond information.
Am I doing something wrong, or is this just Android bug?
btsnoop����������������������ܢ��{� ����������������ܢ���x
�u�
M����
���
���������ܢ����T���.u�P���������������ܢ���T�����������������ܢ��X�T�����������������ܢ��g/T�����������������ܢ��ns ����������������ܢ����
�����(2����
���
���������ܢ���-T�o���t���������������ܢ���T�����
���
���������ܢ���vT����o���t������������������������ܢ����T�����������������ܢ����T����������������ܢ����T�����&���&���������ܢ���VT�"
P�P������������������������������������ܢ��ŔT�����
���
���������ܢ��
`�0���������(�����������������������ܢ���
���������������ܢ�1[>�A��������'�������������������ܢ�1,� A����������������ܢ�1;
� ���������������ܢ�3F�>
�A�����������������������ܢ�3S
A����������������ܢ�3`z�
���
���
���������ܢ�4�o
�A� Y������
���
����������ܢ�x��A����
&����������������ܢ�y�<A ���
&�����������������ܢ�z
A�
����
���������������ܢ�z5� A�������������������������ܢ�z]�� ���������������ܢ�{p
A�����������������ܢ�|-�A
����
�����������������ܢ�|6� ����������������ܢ�|A�
�=�9*
դ����������������ܢ�|_� ����������������ܢ�|y�
��UL��Ya����������������ܢ�|�� ����������������ܢ�|��
��
��A e���������������ܢ�|͊ ����������������ܢ�|�[
�H+�������� ��� ����������ܢ�|��A��A��
�� �� ��5(7фW�Z���C��� ��� ����������ܢ�|�A�
�;��uE._h/-V���AL�xU��D�����������������ܢ�|�A���l�O��h.l�k�����������������ܢ�}��A �
���P���������������������ܢ�}��A������������������ܢ�}�<A�
��������� ��� ���������ܢ�*\A �A��
�eś��#Tc��;�����Zd���������������ܢ�.lA����� ��� ���������ܢ�1�A�J�K�I[���h�����0�;z�&�9����������������ܢ�5_A�k��c Z�.
�~�V���������������ܢ�8�A ����
;�ק�
�y��������������������ܢ�N� ����������������ܢ�`8
�g!P0�Zx���������������ܢ�y� ����������������ܢ��
��Q��ɲ�����������������ܢ���A����g!P0�Zx�Q��ɲ����������������ܢÁc�A ���4CB4����|i�Is���������������ܢÂ+�A�����
���
���������ܢÈ�
>
�A���������������������ܢ�υ�A����
�D
�$b�1�o�������������������ܢ����A ���
�G�f�Tc�PY���B�
��� ��� ���������ܢ����
A�����������WZHP�q�vWR�uA�
���������������ܢ����� ���������������ܢ�А�A����������������ܢ��IcA������������������ܢ��9�A�
� ������(���������������ܢ��uA ���
�
����
���
����������ܢ��}�A����
&����������������ܢ�ؒhA�����������������ܢ�ذEA �
��
Thread State����������������ܢ�شfA�
� ������(���������������ܢ���}A ����
����������������ܢ��
�A�
�������(���������������ܢ��$�A�����������������ܢ��B�A ���� ��
�
�����������������ܢ��FOA�
����
�(��� ��� ���������ܢ�ـ'A ��� �
��*��*��*����������������ܢ�ك�A�
�������(���������������ܢ�ٚ�A����� ��� ���������ܢ�ٻ�A ���������E�P�@B���d�����������������ܢ���QA�
����
�(���������������ܢ���*A ��� � ��*
�
�*����������������ܢ��JA�
���� �(���������������ܢ��,(A�����������������ܢ��K}A ����
����������������ܢ��O A�
���
�
�(���������������ܢ�چrA ���
�
����������������ܢ�ڊA�
���� �(���������������ܢ�ڢ�A����� ��� ���������ܢ���wA ��� �
��*��*��*����������������ܢ��LjA� ���
�
����������������ܢ����A �
��
�*
�)����������������ܢ���aA�
���� �(���������������ܢ���A�����������������ܢ��6MA
� �� � ��*����������������ܢ��9�A� ���
�����
���
���������ܢ��oA �������������������ܢ��s.A�
��� � �(���������������ܢ�ۋ�A�����������������ܢ�۬gA ��� �
����������������ܢ�۰LA�
���
�
�(���������������ܢ����A ���
�
����������������ܢ���A�
���
�
�(���������������ܢ���A�����������������ܢ�� �A
� ��
�
�*����������������ܢ��#jA�
���
�
�(���������������ܢ��[�A ���
�
����������������ܢ��_*A� ���
�
����������������ܢ��x.A�����������������ܢ�ܕ�A
���
�)����������������ܢ�ܙ�A�
������(���������������ܢ���kA ����
����������������ܢ���A�
������(���������������ܢ���&A����� ��� ���������ܢ��
�A ��� �
����E�P�@B��d�����������������ܢ��,A�
������(��� ��� ���������ܢ��GlA ��� �
����E�P�@B��d�����������������ܢ��J�A�
������(���������������ܢ��b�A����� ��� ���������ܢ�݂�A ��� �
����E�P�@B��d�����������������ܢ�݆nA�
������(��� ��� ���������ܢ�ݽ�A ��� �
����E�P�@B��d�����������������ܢ���"A�
������(���������������ܢ���A����� ��� ���������ܢ���A ��� �
����E�P�@B��d�����������������ܢ��tA�
���
���(��� ��� ���������ܢ��Q
A ���
�
����E�P�@B��d�����������������ܢ��T�A�
��� ���(���������������ܢ��i�A����� ��� ���������ܢ�ދ[A ��� !�"����E�P�@B��d�����������������ܢ�ޏ�A�
���"���(��� ��� ���������ܢ���cA ��� $�
%����E�P�@B�� d�����������������ܢ���#A�
���%���(���������������ܢ����A�����������������ܢ���vA ���%�
����������������ܢ��
A� ��������������������ܢ��8"A
����)����������������ܢ��<A� ��������������������ܢ��S�A�����������������ܢ��r�A
����)����������������ܢ��v�A� ��������������������ܢ�߬.A
����)����������������ܢ�߰1A� ��������������������ܢ��ɃA�����������������ܢ����A
����)����������������ܢ���_A� ���
�
����������������ܢ��"�A
���
�)����������������ܢ��&�A� ��� � ����������������ܢ��>@A�����������������ܢ��]iA
��� �)����������������ܢ��aOA� ���#�#����������������ܢ��?A
���#�)����������������ܢ��1A� ���&������������������ܢ�A�����������������ܢ���:A
���&�)����������������ܢ��թA� ���'������������������ܢ��
�A ���'�
���������������ܢ��g A�P�������������������������ܢ��&c� ���������������ܢ��u�A�����
���
���������ܢ��ʂ>
�A���������
���
����������ܢ�+�A����
%����������������ܢ�/�)A�����
���
���������ܢ�0��A ���
����������������ܢ�a�eA����������������ܢ�a�y����������������ܢ�d+�A�
btsnoop����������������������ܢ��[W����
���
���������ܢ��'W��
���������������ܢ���W����
���
���������ܢ� fW��
���������������ܢ�W����
���
���������ܢ�+�W��
���������������ܢ�9�W����
���
���������ܢ�M�W��
���������������ܢ�^]W� ���
���
���������ܢ�f�W�����������������ܢ�rW�
���
���
���������ܢ���W�����������������ܢ��'
����������������ܢ��v
����������������ܢ�ːZ�
@ ��@ ������������������ܢ���Z�����
���
���������ܢ���
@ ����������������ܢ�
�
����������������ܢ�$"
����������������ܢ�<i
����
���
���������ܢ�R�
`�0���������(�����������������������ܢ�R1��
���������������ܢۘ��>�A��������'�������������������ܢۘ�� A����������������ܢۘ�u� ���������������ܢۚ�>
�A�����������������������ܢۛ!L
A����������������ܢۛM1�
���
���
���������ܢۜy�
�A� Y������ ��� ���������ܢۜ��
A�����������WZHP�q�vWR�uA�
���������������ܢۜ�W� ���������������ܢ۟haA�����������������ܢ��Z�A �
���P����������������������ܢ��mA�
���������������������ܢ��� A�P�������������������������ܢ���� ���������������ܢ��kA�����
���
���������ܢ��>
�A���������
���
����������ܢ�.V�A����
&����������������ܢ�2�A ���
&�����������������ܢ�2/pA�
����
���������������ܢ�2>b A�������������������������ܢ�2H�A�����������������ܢ�2XO� ���������������ܢ�;*�A
����
�����������������ܢ�;7� ����������������ܢ�;@>
���e��j�)���������������ܢ�;J- ����������������ܢ�;`�
��\�x�������������������ܢ�;{� ����������������ܢ�;�
��
���"���������������ܢ�;�� ����������������ܢ�;�tA�����������������ܢ�;�d
�d�Y�);����� ��� ����������ܢ�;�eA��A��
΅S)���(&u��ì������ ��� ����������ܢ�;�}A��
u��G�2b��T�3�����H%
7�
����������������ܢ�<
8A�a|7\�-�3\]A������������������ܢ�>5�A����� ��� ���������ܢ�A<?A �A��
�eś��#Tc��;�����Zd��� ��� ���������ܢ�A@}A�J�K�I[���h�����0�;z�&�9����������������ܢ�AD
A�k��c Z�.
�~�V���������������ܢ�AGBA �����j%]��*��o��)|���������������ܢ�AZ� ����������������ܢ�Ab�
���/���\^���������������ܢ�Ax ����������������ܢ�A��A�����������������ܢ�A��
�w
��?��D����������������ܢ�A�{A������/���\^w
��?��D���������������ܢ�G3A�����������������ܢ�GLA �����T.@8�Ǯ��c����
���
���������ܢ�n��>
�A���������������������ܢ�~�
A����
�-��
-���8C�����������������ܢ�A ���
��.Ƒ)��k$�J�6��� ��� ���������ܢ�
A�����������_!0
(�K�B���3����������������ܢ�2h� ���������������ܢ��*�A����������������ܢ܂U�A������������������ܢ܇�BA�
� ������(���������������ܢ܇��A ���
�
����
���
����������ܢ܇�8A����
&����������������ܢ܇�qA�����������������ܢ܇��A �
��
Thread State����������������ܢ܇��A�
� ������(���������������ܢ܈m�A ����
����������������ܢ܈r�A�
�������(���������������ܢ܈��A�����������������ܢ܈�gA ���� ��
�
�����������������ܢ܈�xA�
����
�(��� ��� ���������ܢ܈�tA ��� �
��*��*��*����������������ܢ܈�A�
�������(���������������ܢ܉$�A����� ��� ���������ܢ܉>�A ���������E�P�@B���d�����������������ܢ܉DA�
����
�(���������������ܢ܉z'A ��� � ��*
�
�*����������������ܢ܉�A�
���� �(���������������ܢ܉��A�����������������ܢ܉�mA ����
����������������ܢ܉�CA�
���
�
�(���������������ܢ܉��A ���
�
����������������ܢ܉�kA�
���� �(���������������ܢ܊
�A����� ��� ���������ܢ܊*�A ��� �
��*��*��*����������������ܢ܊/�A� ���
�
����������������ܢ܊bSA �
��
�*
�)����������������ܢ܊g
A�
���� �(���������������ܢ܊;A�����������������ܢ܊�vA
� �� � ��*����������������ܢ܊��A� ���
�����
���
���������ܢ܊�QA �������������������ܢ܊�OA�
��� � �(���������������ܢ܊�_A�����������������ܢ܋�A ��� �
����������������ܢ܋
A�
���
�
�(���������������ܢ܋L�A ���
�
����������������ܢ܋RhA�
���
�
�(���������������ܢ܋h�A�����������������ܢ܋��A
� ��
�
�*����������������ܢ܋��A�
���
�
�(���������������ܢ܋��A ���
�
����������������ܢ܋��A� ���
�
����������������ܢ܋ޱA�����������������ܢ܋�uA
���
�)����������������ܢ܌�A�
������(���������������ܢ܌TfA ����
����������������ܢ܌Y�A�
������(���������������ܢ܌qVA����� ��� ���������ܢ܌��A ��� �
����E�P�@B��d�����������������ܢ܌��A�
������(��� ��� ���������ܢ܌�A ��� �
����E�P�@B��d�����������������ܢ܌�/A�
������(���������������ܢ܌�sA����� ��� ���������ܢ܍�A ��� �
����E�P�@B��d�����������������ܢ܍
A�
������(��� ��� ���������ܢ܍ApA ��� �
����E�P�@B��d�����������������ܢ܍F[A�
������(���������������ܢ܍[�A����� ��� ���������ܢ܍{�A ��� �
����E�P�@B��d�����������������ܢ܍�1A�
���
���(��� ��� ���������ܢ܍�jA ���
�
����E�P�@B��d�����������������ܢ܍��A�
��� ���(���������������ܢ܍�%A����� ��� ���������ܢ܍�EA ��� !�"����E�P�@B��d�����������������ܢ>A�
���"���(��� ��� ���������ܢHjA ��� $�
%����E�P�@B�� d�����������������ܢ^TA�
���%���(���������������ܢ�A�����������������ܢ��A ���%�
����������������ܢ��A� ��������������������ܢ�UA
����)����������������ܢ �A� ��������������������ܢ/�A�����������������ܢM
A
����)����������������ܢb�A� ��������������������ܢ�A
����)����������������ܢ�UA� ��������������������ܢ�@A�����������������ܢ��A
����)����������������ܢܐ8A� ���
�
����������������ܢܑz"A
���
�)����������������ܢܑ�EA� ��� � ����������������ܢܑ�A�����������������ܢܑѸA
��� �)����������������ܢܑ��A� ���#�#����������������ܢܒ��A
���#�)����������������ܢܒ�A� ���&������������������ܢܓO8A�����������������ܢܓk�A
���&�)����������������ܢܓoLA� ���'������������������ܢܓ��A ���'�
���������������ܢܓ�� A�P�������������������������ܢܓ��� ���������������ܢܗQ�A�����
���
���������ܢܘ5[>
�A���������������������ܢܹ�
A �
���P����������������������ܢܹ�pA�
���������������������ܢܹ�� A�P�������������������������ܢܹ��� ���������������ܢܼ$�A����������������ܢܼ-�����������������ܢܼ�
A�����������������ܢܼ�T�A�