Hi there,
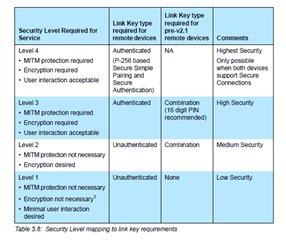
I am adding security to my service characteristic and i found that for security mode 1 level 4, bonding is required in order to access characteristic values. Is it the same case for level1- level3, can i separate characteristic and bonding? eg. add different security level to characteristic and bonding and bond two devices only when i want to? I am using nRF52832 and SDK14.00.