Hi,
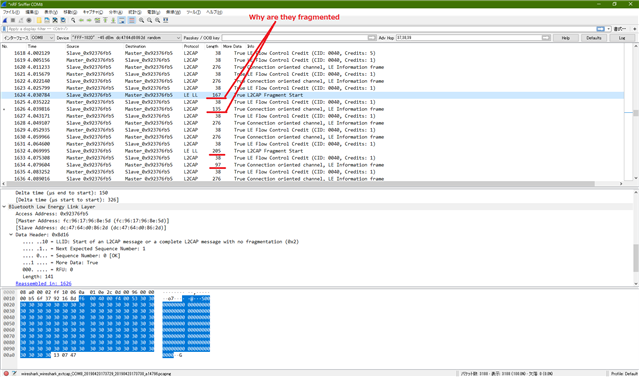
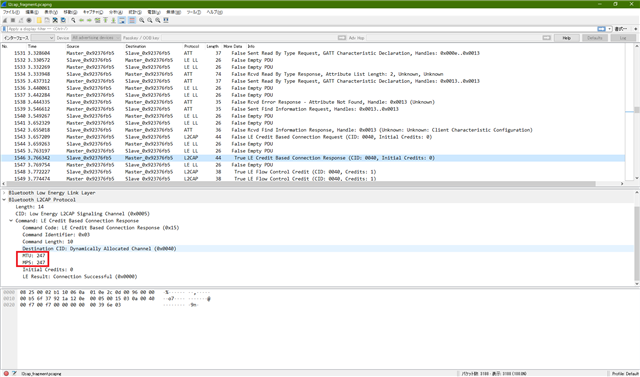
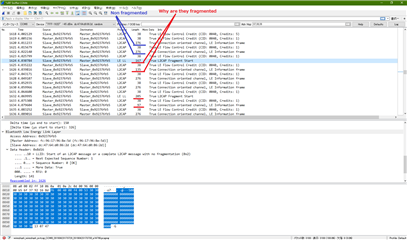
I have been testing l2cap.
Why is it fragmented by softdevice.
+---------------------+ +---------------------+
| PCA10040(nRF52832) |....... L2CAP .......| PCA10040(nRF52832) |
| | | |
| repeat tx_func() | | |
+---------------------+ +---------------------+
PCA10040(nRF52832)
SDK15.3
Softdevice S132 v6.1.1
tx_func(){
static uint8_t send_buf[244];
static ble_data_t obj;
memset(send_buf, '0', sizeof(send_buf));
send_buf[0] = 'S';
send_buf[sizeof(send_buf)-1] = 'E';
obj.p_data = send_buf;
obj.len = sizeof(send_buf);
while(NRF_SUCCESS == sd_ble_l2cap_ch_tx(m_conn_handle, local_cid, &obj));
}