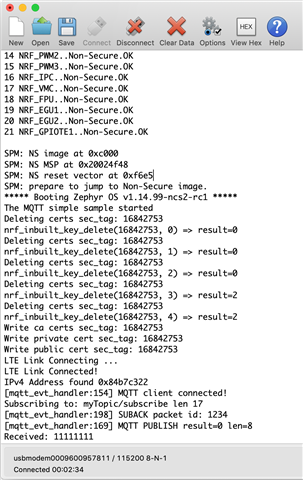
I'm working on a project using nRF9160 DK.
How can you use MQTT+TLS in nRF9160?
Where should ca certificate file be stored?
I modified the code below in mqtt_simple project. What code should I modify additionaly?
<prj.conf> CONFIG_MQTT_LIB_TLS=y
<main.c>
/**@brief Initialize the MQTT client structure
*/
static void client_init(struct mqtt_client *client)
{
mqtt_client_init(client);
broker_init();
/* Add from here */
static struct mqtt_utf8 password;
static struct mqtt_utf8 user_name;
password.utf8 = (u8_t *)MQTT_PASSWORD;
password.size = strlen(MQTT_PASSWORD);
user_name.utf8 = (u8_t *)MQTT_USERNAME;
user_name.size = strlen(MQTT_USERNAME);
/* to here */
/* MQTT client configuration */
client->broker = &broker;
client->evt_cb = mqtt_evt_handler;
client->client_id.utf8 = (u8_t *)CONFIG_MQTT_CLIENT_ID;
client->client_id.size = strlen(CONFIG_MQTT_CLIENT_ID);
client->password = &password; // Add here
client->user_name = &user_name; // Add here
client->protocol_version = MQTT_VERSION_3_1_0; // originally MQTT_VERSION_3_1_1
/* MQTT buffers configuration */
client->rx_buf = rx_buffer;
client->rx_buf_size = sizeof(rx_buffer);
client->tx_buf = tx_buffer;
client->tx_buf_size = sizeof(tx_buffer);
/* MQTT transport configuration */
/* MODIFIED HERE */
#if defined(CONFIG_MQTT_LIB_TLS)
client->transport.type = MQTT_TRANSPORT_SECURE;
client->transport.tls.config.peer_verify = 0;
client->transport.tls.config.cipher_count = 0;
client->transport.tls.config.cipher_list = NULL;
client->transport.tls.config.sec_tag_count = 0;
client->transport.tls.config.seg_tag_list = NULL;
client->transport.tls.config.hostname = NULL;
#else
client->transport.type = MQTT_TRANSPORT_NON_SECURE;
#endif
}