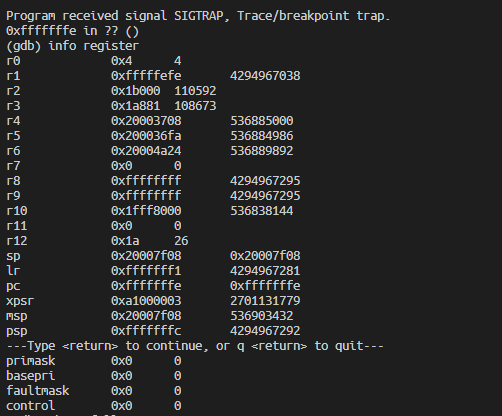
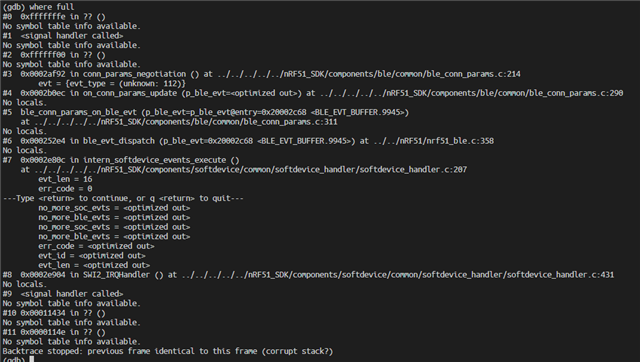
Hello, my old question: https://devzone.nordicsemi.com/f/nordic-q-a/48087/nrf51822-s130-hardfault-error
I found something.
After removing -fdata-sections in makefile, Hardfault error in my old question never occur.
What is role of data-sections flag?
I want to know purpose and role of this flag.
From https://gcc.gnu.org/onlinedocs/gcc-2.95.2/gcc_2.html#SEC10
-ffunction-sections-fdata-sectionsPlace each function or data item into its own section in the output file if the target supports arbitrary sections. The name of the function or the name of the data item determines the section's name in the output file.
Use these options on systems where the linker can perform optimizations to improve locality of reference in the instruction space. HPPA processors running HP-UX and Sparc processors running Solaris 2 have linkers with such optimizations. Other systems using the ELF object format as well as AIX may have these optimizations in the future.
Only use these options when there are significant benefits from doing so. When you specify these options, the assembler and linker will create larger object and executable files and will also be slower. You will not be able to use gprof on all systems if you specify this option and you may have problems with debugging if you specify both this option and `-g'.