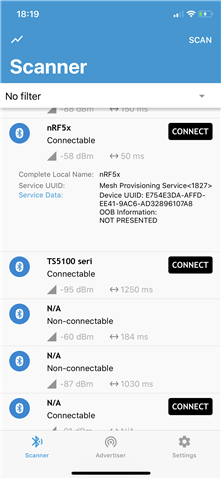
I'm struggling with how to properly identify an unprovisioned mesh device. Basically when i scan for unprovisioned devices from my iOS app, I'd like for only our devices to show up, not any random mesh device. I'm still struggling to understand all the terminology, but if I understand everything correctly, I should be checking the `p_device_uri` set in `mesh_provisionee_prov_start` against the advertised data, or something. According to the mesh spec, it seems like this data is hashed using the salt function `s1`, which I think corresponds to `OpenSSLHelper.calculateSalt` in the iOS SDK. However, what I'm not understanding is which data to actually check against and how. So far, when I discover unprovisioned proxy nodes, I can do this:
func centralManager(_ central: CBCentralManager,
didDiscover peripheral: CBPeripheral,
advertisementData: [String: Any],
rssi RSSI: NSNumber) {
if let serviceData = advertisementData[CBAdvertisementDataServiceDataKey] as! [CBUUID: NSData]? {
let provisioningData = serviceData[MeshServiceProvisioningUUID]
print("service data: \(provisioningData)")
}
}
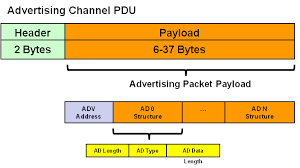
`provisioningData` contains some bytes of data, for me it returned `E754E3DAAFFDEE419AC6AD32896107A80000`, Which is 18bytes. The mesh spec seems to define the beacon format as follows:

But this comes out to 23 bytes, so it can't really match the format of the data I received.
It seems that the nRF Connect application is able to decipher at least some of this data, since it shows the device UUID in its scan view, but since the source of this app is not available I can't check against it.
Any help would be appreciated!