Hi,
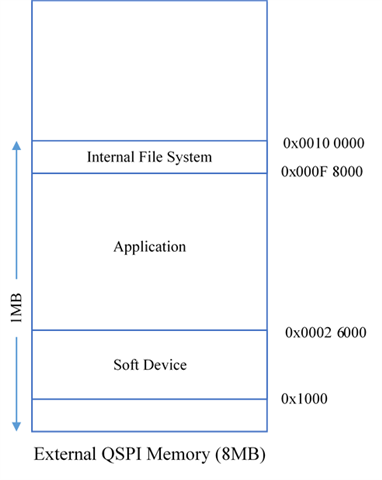
I am working on project, in which we using nordic nRF52840 chip. We need to flash the app+SD+BL image file in external QSPI memory.
After prevalidation, the DFU controller starts to send flash image package, we need to receive this and need to save in external QSPI memory. Once the postvalidation is successful, then read all the flash image package stored in external QSPI memory and write it to internal flash memory.
For that we use secure bootloader example code as reference file. I need to know where i need to modify the secure bootloader code.
I noticed that after prevalidation, the flash is erased in on_data_obj_create_request() function in nrf_dfu_req_handler.c file, and flash is written in on_data_obj_write_request() under the same c file. Is that right?
Thanks & Regards
Mohammad Gouse