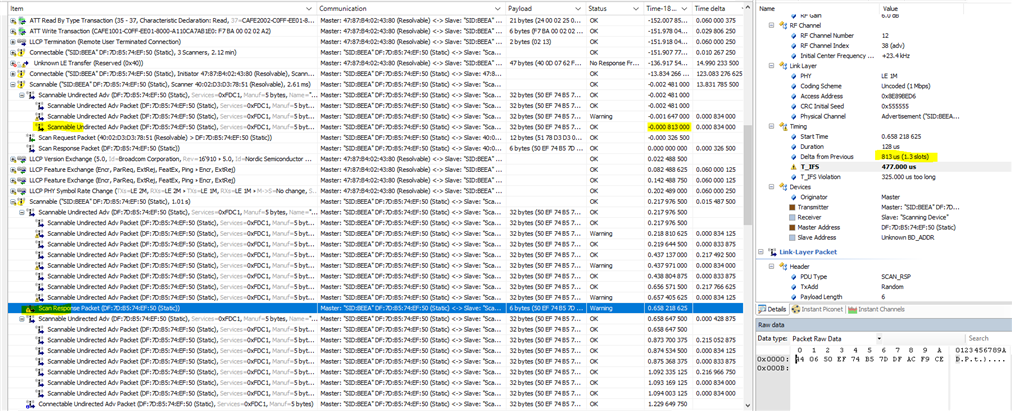
My bluetooth analyzer is showing that my peripheral's scan response packets have a T_IFS Violation 326.125 us too long. I don't use scan response data for anything but I want to understand why I am seeing this and if I can fix it.
Name Value
Link-Layer Information
Sniffer Radio
RX Strength (RSSI) -40.0 dBm
RX Quality High
RF Gain 6.0 dB
RF Channel
RF Channel Frequency 2402 Mhz
RF Channel Number 0
RF Channel Index 37 (adv)
Initial Center Frequency Offset -7.81 kHz
Link Layer
PHY LE 1M
Coding Scheme Uncoded (1 Mbps)
Access Address 0x8E89BED6
Received Access Address 0x8E89BED6
CRC Initial Seed 0x555555
Physical Channel Advertisement ("SON:82CE" F5:92:E4:62:F1:13 (Static))
Timing
Start Time 2,390.597 964 000
Duration 128 us
Delta from Previous 814.13 us (1.3 slots)
T_IFS 478.125 us
T_IFS Violation 326.125 us too long
Devices
Originator Master
Transmitter Master: "SON:82CE" F5:92:E4:62:F1:13 (Static)
Receiver Slave: "Scanning Device"
Master Address F5:92:E4:62:F1:13 (Static)
Slave Address Unknown BD_ADDR
Link-Layer Packet
Header
PDU Type SCAN_RSP
RFU Reserved (0)
RFU (ChSel) Reserved (0)
TxAdd Random
RFU (RxAdd) Reserved (0)
Payload Length 6
Advertiser Address F5:92:E4:62:F1:13 (Static)
Scan Response Data
Non-significant Part 0 bytes
CRC Valid
Raw Content
Raw Data 44 06 13 F1 62 E4 92 F5 03 F8 3E
Whitened Raw Data C9 D4 44 50 5F 43 F4 45 76 C9 2F