Hello, I'm developing application starting from blinky example extracted from nRF5_SDK_15.3.0_59ac345 SDK.
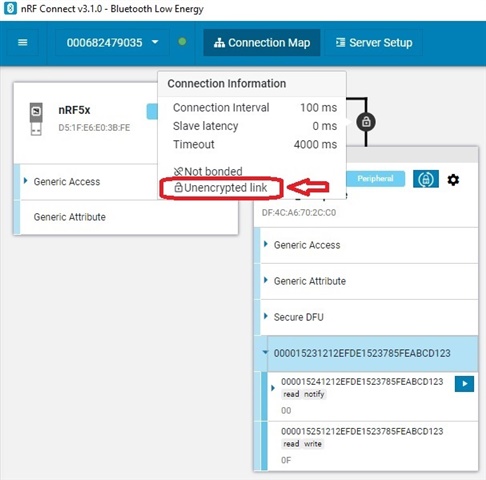
I see (using nRF Connect) that the connection result as "unencrypted link" (image here below)
How can I make the link secured with encryption? There is an example on SDK that show how to make it?
Thanks
A. Barbieri - Italy