Hi
I am currently testing Buttonless DFU using SDK 12.3, nRF52832 DK.
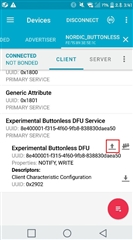
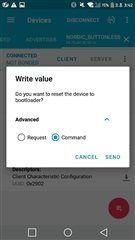
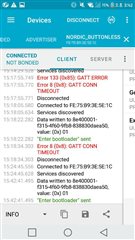
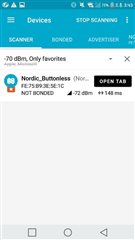
Example test was conducted first using the DK board, but as you can see in the picture, it will fail. I don't know why.
Is the method wrong?
Hi
I am currently testing Buttonless DFU using SDK 12.3, nRF52832 DK.
Example test was conducted first using the DK board, but as you can see in the picture, it will fail. I don't know why.
Is the method wrong?



