Security of data passing in BLE communication
Hello
I am developing based on "multirole lesc" of BLE sample project.
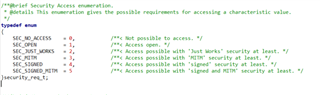
What is worrisome about the project is the "security_req_t" structure in "ble_srv_common.h".
I think that this structure is where security is set when reading and writing data, but data cannot be sent in the following configuration.
1.PERIPHERAL (SEC_MITM) ⇔Multirole (SEC_MITM)
2.Multirole (SEC_MITM) ⇔Central (??: There is no place to set)
In case of 1, it will succeed when the peripheral and Multirole are “SEC_OPEN”, but is there any superiority or inferiority relationship?
In case 2, Multirole succeeds when “SEC_OPEN”, but can CENTRAL project be other than SEC_OPEN? Please let me know if there is a setting method.
Is this structure related to the communication security mode and security level?
The environment is as follows.
SoftDevice: S132
IDE: SES
BLE Device: NRF52832
SDK version: 15.30
peripheral project: ble_peripheral⇒ble_app_hrs
multirole project: experimental⇒ble_app_multirole_lesc
central project: ble_central⇒ble_app_hrs_c
Thank you.