I received the device and tried running the default asset tracker that was installed and kept getting these messages:
DEBUG modem << Connected to LTE network\x0D\x0A
DEBUG modem << [00:00:06.666,076] \x1B[0m<dbg> nrf_cloud_transport.nct_connect: IPv4 Address ...
DEBUG modem << cloud_connect failed: -111\x0D\x0A
DEBUG modem << LTE link disconnect\x0D
First I tried updating the modem firmware and application to the newest versions but that did not help.
I read a few posts about the certificates and my device did not list any. I installed the at_client example and tried loading new certificates on, I was successful only once but unfortunately I generated the certificates wrong.
After hundreds of reboots of the device most of the time when opening the Link Monitor I only get this displayed in the terminal and all commands entered will timeout:
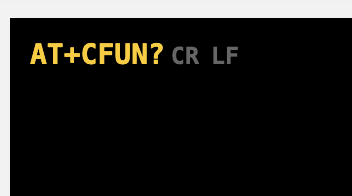
98% of the time I cannot run any commands, but when I am able to run a few simple commands like display the modem firmware version, or list certificates, when I then try to load on the new certificates I get the timeout again and no further commands work.
This is getting very frustrating, any help would be greatly appreciated.


