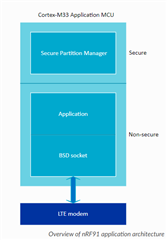
- Does secure boot prevent an acquired device from being debugged using JTAG, can a hacker view running code and variables in memory?
What is the best way to store these so they can be formatted into a connection string using sprintf (that goes over TLS)? Clearly string formatting will
require these to be brought into SRAM. Would the KMU be the best approach to store these assuming it is available for Secure Boot? There don't appear to be any working C examples of
this being used, are there any? As they're being brought into SRAM and potentially viewed using a debugger is the only benefit of using KMU to prevent casual browsing
of the flash storage for secrets? Any other recommendations?
the provisioning from the CERTIFICATES_FILE, and then switch over the Secure?