Hello
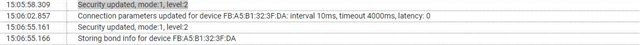
Pairing: Just Works with Bonding: Passkey Entry, Peripheral Displays works for bonding.
I want to make LESC Pairing: Just Works with Bonding. Is it possible? According to the documentation from Nordic this is not possible for LESC pairing with Just works to have a secure bonded device.
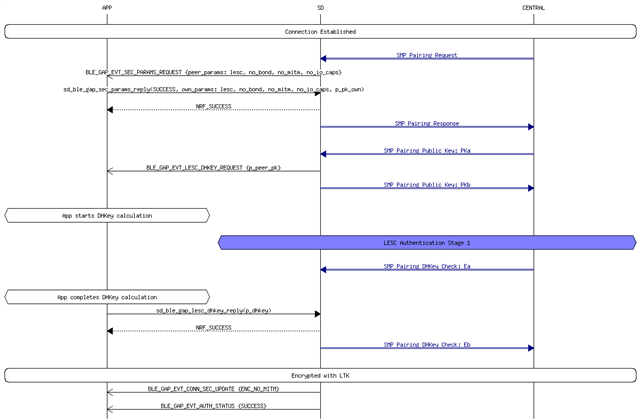
If this is possible, please let me know how can I do it. I want to bond and pair device with LESC "Just Works" with a button press.