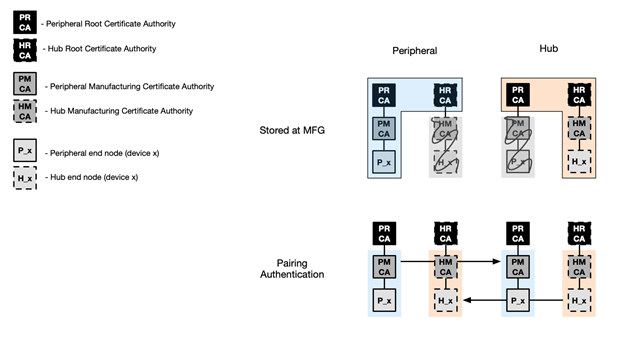
Hi All,
- Any reason not to go this route, or is there a better alternative for this problem?
- Does anyone have any resources to facilitate this type of development that they can point me to?
- If x.509 certificates are used for initial authentication, should I still use the LE Secure Connections + Long Term Key (LTK) standards for the subsequent encryption and any future bonding?
Any suggestions would be helpful.
Thanks
jay