Hi,
I am using an nrf52840 MCU, Nordic SDK 16.0.0 and IAR Workbench for ARM v8.40.1.
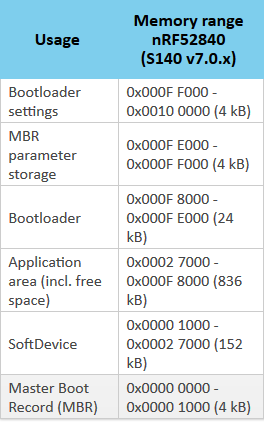
The MCU has the following configuration:
- MBR installed
- DFU secure bootloader (USB only) installed and functional
- Bootloader settings installed
For the main application, I'm trying to use the example blinky application. The main application is downloaded via the Segger interface using IAR.
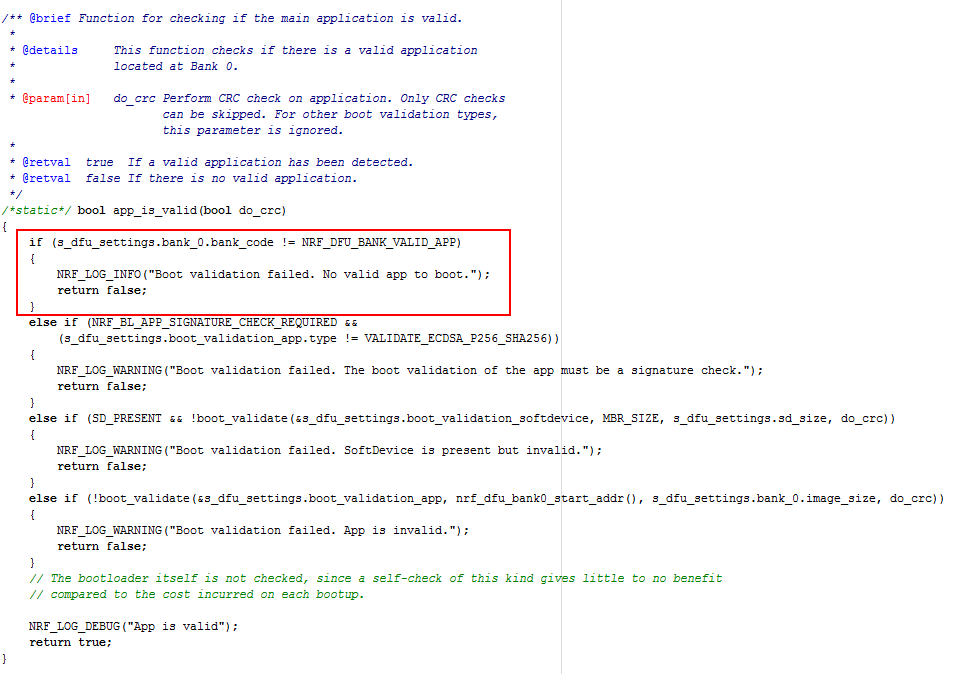
Using the above setup, my issue is that the blinky application does not execute at all - even after a power cycle.
If I erase the secure bootloader and its settings, leaving only the MBR, the blinky application then executes correctly, e.g.:
1. Erase the entire flash
nrfjprog.exe --family NRF52 --eraseall
Output:
Erasing user available code and UICR flash areas.
Applying system reset.
2. Program the MBR
nrfjprog --reset --program mbr.hex --family NRF52 --sectoranduicrerase
Output:
Parsing hex file.
Erasing page at address 0x0.
Applying system reset.
Checking that the area to write is not protected.
Programming device.
Applying system reset.
Run.
3. Program Blinky App
nrfjprog --reset --program blinky_pca10056_mbr.hex --family NRF52 --sectoranduicrerase
Output:
Parsing hex file.
Erasing page at address 0x1000.
Applying system reset.
Checking that the area to write is not protected.
Programming device.
Applying system reset.
Run.
The ROM settings for the blinky example is: 0x1000 - 0xfffff
The RAM settings for the blinky example is: 0x20000008 - 0x2003ffff
Any ideas what I'm missing?
Thanks to all in advance.