 android large mtu.pcapnghp pavilion ble 5.pcapng
android large mtu.pcapnghp pavilion ble 5.pcapng
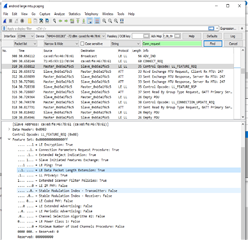
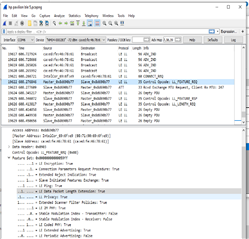
After the MTU size exchange of 247 bytes with Android LL_LENGTH_REQ/LL_LENGTH_RSP are exchanged with 123 byte octets for TX and RX. Data flows properly after that.
But with Windows, after the MTU size exchange of 247 bytes an LL_LENGTH_REQ is sent with 251 byte octet. No LL_LENGTH_RSP is sent by Nordic from the nRF52832
and no further data exchange takes place.


