Hi,
Recently, I am studying the blog as the link below:
https://docs.microsoft.com/en-us/windows-hardware/design/component-guidelines/bluetooth-prepairing
We would like to do pre-paired in factory.
As you might see from the website, it has mentioned that as peripheral it is required to follow the rule.
Peripheral
- Bluetooth LE
- Store for Device ID (hashed from Bluetooth Address) & TK value
- Custom Advertisement (defined below)
I am unclear about the Device ID description.
DeviceID: uniquely identify a supporting device and should be 8 bytes in length to avoid device conflicts.
From the description it said it should be 8 bytes, but the BT address should be 6 bytes (0xC7BB9B6D8833).
I suppose I am misunderstanding. Could you give me some guide?
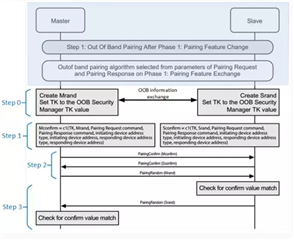
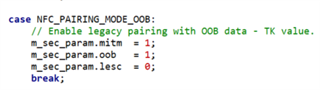
And I would like to know whether I could check and set the the Device ID as well as the temporary key (SMP TK)?
If there is any API, could you help me to indicate?
Thanks.