Hello,
I am currently working on a product with nRF51822 chip, based on SDK10.0.0. The problem is, after a firmware update, my device fails to reconnect to an Android mobile, even though the bonding information is preserved.
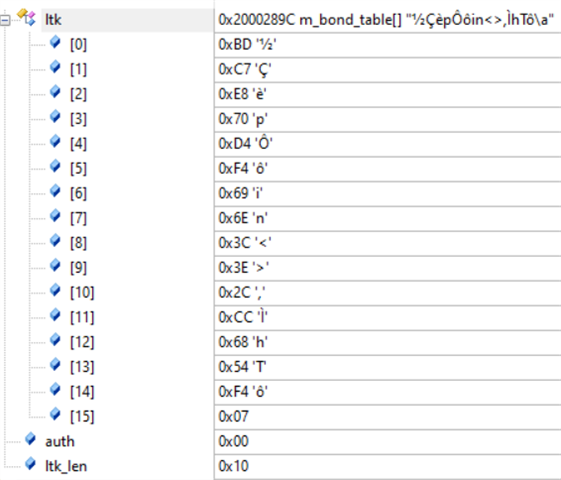
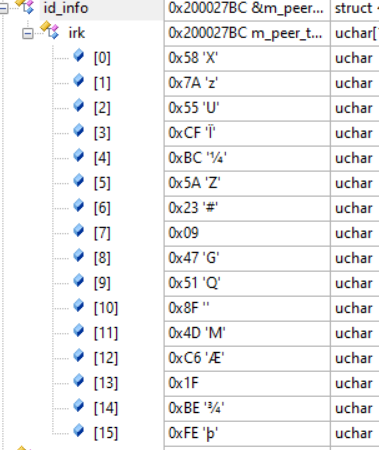
The bootloader is the same as the DFU example provided in the SDK with some adaptations for HW. It preserves application data (bonding information for BLE mainly). Before the firmware update begins, my device is bonded with an Android mobile and they can communicate with each other.
However, after a firmware update, when I try to reconnect to the Android mobile, it always sends me a pairing request, as if it did not know my device. After this pairing procedure, they still fail to communicate with each other. Only after deleting the bonding information on my device can they pair with each other correctly again and start to communicate.
I am sure that the bonding data are correctly preserved on my device, because an IOS mobile can reconnect successfully after firmware update. As far as I know, the APP on Android mobile does not delete bonding information either.
So I would like to ask, it there any behaviour in the updating process that might lead an Android mobile to believe that the updated device is a new device?