Hi,
I was tracking down a bug that resulted in a secure fault exception. To save some time tracking it down I enabled logging in the spm. However this resulted in an escalated exception in the spm fault handler. As far as I can see the MCU is in non-secure state when the fault handler in the spm is about to print out the original secure fault exception, this results in an elevated hard fault:
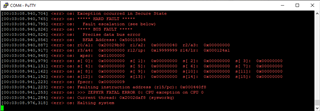
The BFAR address 0x50015504 indicates that the problem is accessing the RTC1_S. Below I have braked the spm code just before the exception gets elevated. This is just before it is about to get a timestamp for a log printout. If I at this point check access to RTC1_S and RTC1_NS using the debugger I can see that RTC1_NS is accessible but RTC1_S is not. For this reason I think the MCU is still in non-secure mode, and as the MCU is executing in the spm code I assume it always will use the secure version of all the HW (in this case RTC1_S).
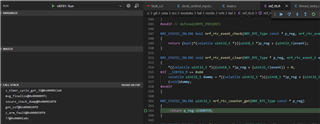
We are using the nRF9160 sample spm module. In this module I have only added the following config:
CONFIG_LOG=y
CONFIG_SPM=y
volatile uint32_t dummy = *((uint32_t *) 0x5000F000);


