I'm new to the nRF5340 and zephyr and ncs, but I have gone through the tutorial series https://devzone.nordicsemi.com/nordic/nrf-connect-sdk-guides/b/getting-started/posts/nrf-connect-sdk-tutorial
We're developing a product that will use the SPIS peripheral on the nRF5340 and I have a few nRF5340-PDK boards
Since I haven't found any SPIS sample projects, I started with the zephyr adxl372 sensor sample project.
I wanted to get it to a point where the SPIM peripheral was working (wiggling pins as expected) then create my own sensor and change it to SPIS.
I re-mapped the SPI pins to pins on port 1.
I started by using the non-secure build, but couldn't get any SPI activity on the pins.
It looked like the chip select pin was being handled as a GPIO pin (rather than as part of the SPIM peripheral) and when I tried to manually change registers in the GPIO1 peripheral through the SES through the registers view, all the SPIM1 registers showed as 0 and I couldn't change them.
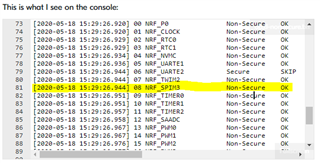
I wondered if GPIO1 was not under the application processor's control, because the NRF_P1 is missing from the peripheral domain status printed at bootup.
Peripheral Domain Status
00 NRF_P0 Non-Secure OK
01 NRF_CLOCK Non-Secure OK
02 NRF_RTC0 Non-Secure OK
03 NRF_RTC1 Non-Secure OK
04 NRF_NVMC Non-Secure OK
05 NRF_UARTE1 Non-Secure OK
06 NRF_UARTE2 Secure SKIP
07 NRF_TWIM2 Non-Secure OK
08 NRF_SPIM3 Non-Secure OK
09 NRF_TIMER0 Non-Secure OK
10 NRF_TIMER1 Non-Secure OK
11 NRF_TIMER2 Non-Secure OK
12 NRF_SAADC Non-Secure OK
13 NRF_PWM0 Non-Secure OK
14 NRF_PWM1 Non-Secure OK
15 NRF_PWM2 Non-Secure OK
16 NRF_PWM3 Non-Secure OK
17 NRF_IPC Non-Secure OK
18 NRF_VMC Non-Secure OK
19 NRF_FPU Non-Secure OK
20 NRF_EGU1 Non-Secure OK
21 NRF_EGU2 Non-Secure OK
22 NRF_DPPIC Non-Secure OK
23 NRF_GPIOTE1 Non-Secure OK
24 NRF_REGULATORS Non-Secure OK
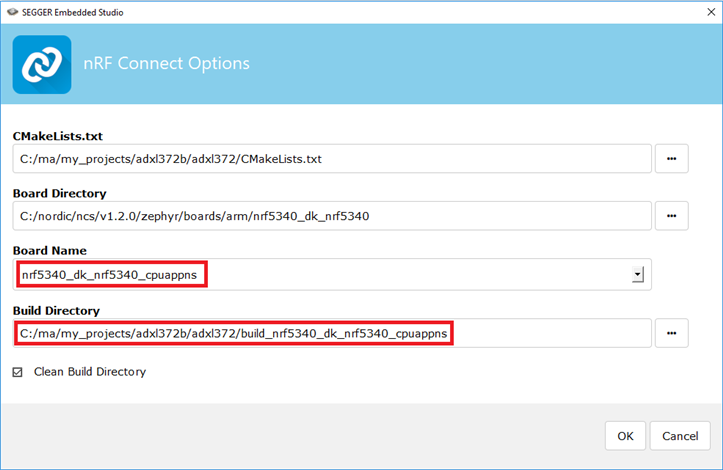
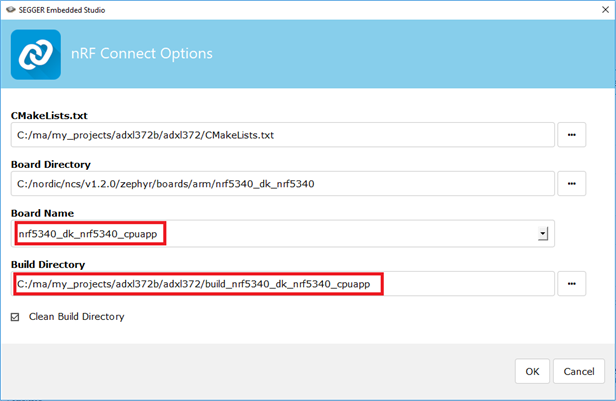
When I choose Project > Configure nRF Connect SDK Project (in the non-secure project) it shows two options - menuconfig and spm_menuconfig
I tried the secure build, and then I saw SPI activity.
But when I try to view the configuration with Project > Configure nRF Connect SDK Project (in the secure project) it does not show me two options. It just takes me to a config.
Q1: Why doesn't the non-secure project work to control the SPI pins?
Q2: Why doesn't the secure project show both menuconfig and spm_menuconfig?