Hi,
I am using nRF52840, S140 V7.0.1.
I am using Secure Serial Bootloader and able to do DFU of Application.
DFU of application
Using below command able to generate DFU package.
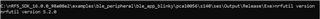
nrfutil pkg generate --hw-version 52 --application-version 2 --application ble_app_blinky_pca10056_s140.hex --sd-req 0xCA --key-file private.key BLE_Beeper_V2_package.zip
Once Package is generated, able to do DFU via below command
nrfutil dfu serial -pkg BLE_Beeper_V2_package.zip -p COM8 -b 115200 -fc 0
DUF of Bootloader
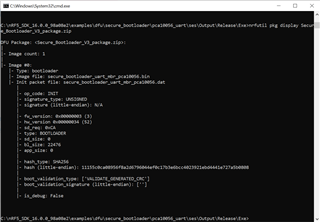
Now I am trying to do the same for generating Bootloader package. Generate Bootloader DFU package
nrfutil pkg generate --hw-version 52 --bootloader-version 3 --bootloader secure_bootloader_uart_mbr_pca10056.hex --sd-req 0xCA --key-file private.key Secure_Bootloader_V3_package.zip
I am trying to do Bootloader DFU using below commands.
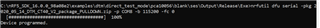
nrfutil dfu serial -pkg Secure_Bootloader_V3_package.zip -p COM8 -b 115200 -fc 0
But Bootloader DFU is not success. Below is the snapshot.
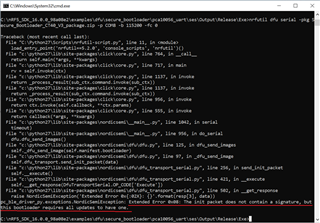
But I am able to do DFU of my application.
1) Is there any issue in generating boot-loader DFU package and loading.
2) As per below link I used version 3 as, already loaded bootloader version is 2. In bootloader code is there any version macro where I need to change to 3.
But above macro NRF_DFU_APP_DOWNGRADE_PREVENTION I am seeing “This does not apply the bootloader updates.” I am bit confused. Whether bootloader version should always be greater.
Thanks & Regards
Vishnu Beema