Hi!
Can't continue here:
So I've made a new question.
Thanks Einar for answering!
Using SDK16 and S132 with Segger Embedded Studio.
Managed to "ravage" the secure bootloader and create my own, so called "background bootloader". Still in development phase but according to my knowledge the thing should work.
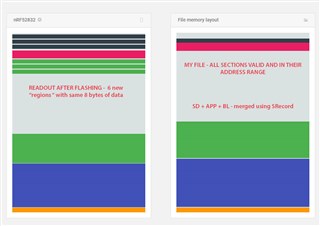
I've managed to merge Softdevice, Application and Bootloader to a single hex file which we use for initial programming. And I have no problem starting the Bootloader and then switching to application, at least so far.
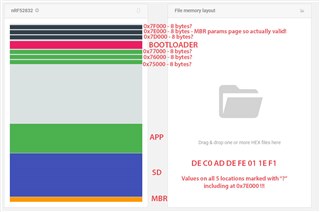
After flashing the file to nRF52832 I get 6 new locations in flash at which same 8 bytes of data can be found.
Address 0x7E000 (MBR PARAMS PAGE) is the only one which should be populated to some degree since I've removed bootloader settings section. My bootloader stores it's data in EEPROM.
I've attached 2 images with more explanation.
I've checked everything I could think of including Section Placement Macros and Memory Segments in SES but just can't find why are addresses 0x75000, 0x76000, 0x77000, 0x7D000 and 0x7F000 are populated with same pattern: DE C0 AD DE FE 01 1E F1.
Would like to know what they are, why are they there and how to remove them, if possible.
Thanks!


