Hello,
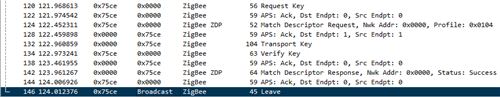
I am developing a zigbee coordinator with a BMD340 module (using the nRF52840). I want to support several third party device with the coordinator. I am able to connect and use an Elko thermostat and Elko dimmer. But I try to connect and use an Elko PIR sensor, and it keeps joining and leaving the network (even if the authorization status is 0). Legacy is enabled (using bdb legacy enable command). What could be the issue? I tried to use an Xbee dongle for testing, and it joins the network normally.
I also noticed that sometimes the different signals when new device join the network are happening several times.
BR,
Damien