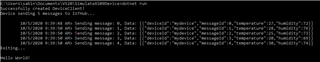
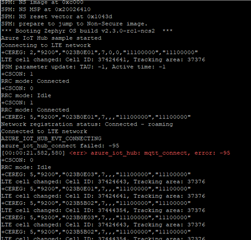
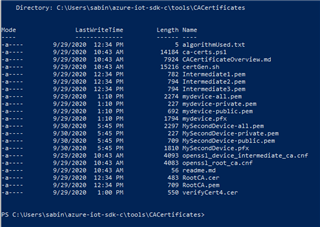



Hi Sabine,
In our docs about Azure we point to this link to get the certificates.
In that page there is a link to "Managing test CA certificates for samples and tutorials" which has the scripts used and the explanations you are looking for.
So the following is needed to get it to work with PowerShell-generated certs:
"RootCA.pem" has to be uploaded to the IoT Hub and verified.
For bash-generated certs, then the following is needed:
certs/new-device.cert.pemprivate/new-device.key
Best regards,
Martin L.
Hi Sabine,
In our docs about Azure we point to this link to get the certificates.
In that page there is a link to "Managing test CA certificates for samples and tutorials" which has the scripts used and the explanations you are looking for.
So the following is needed to get it to work with PowerShell-generated certs:
"RootCA.pem" has to be uploaded to the IoT Hub and verified.
For bash-generated certs, then the following is needed:
certs/new-device.cert.pemprivate/new-device.key
Best regards,
Martin L.
Here we go - Success!
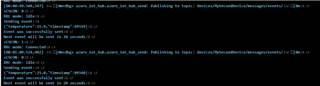
Thank you for the clarification. Sabine Urquhart