Hi everyone,
I am interacting with the ble_app_hrs in order to learn about bonding. I am using nRF52840 DK as a peripheral and donggle (nRF52840) as central along with the nRF Connect for Desktop.
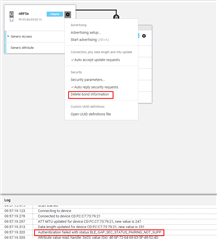
I can perform pairing and bonding with success. However I've noticed that when I select "Delete bond information" then I am not able neither to pair nor to bond anymore and the Error "BLE_GAP_SEC_STATUS_PAIRING_NOT_SUPP" is appeard on the log menu.
In order to work around this issue I have delete bonds from peripheral's side by pressing Button 2 during resetting .. Why I have to do this? I mean, this is the case when central deletes bond information (the peripheral must delete too)? How can I automate this procedure (my future application won't have any button to erase bonds)?
Thanks in advance
Nick


