Hi,
I have been struggling with this for 2 days now, and I cannot get my head around the problem.
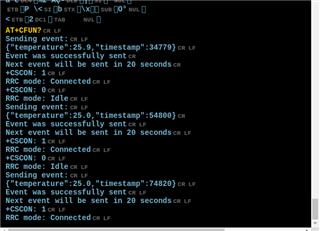
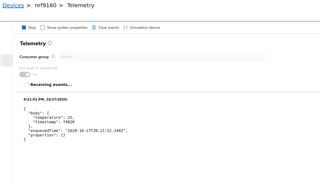
I want to send data from my nrf9160-dk to Azure IoT Hub via the sample application: https://developer.nordicsemi.com/nRF_Connect_SDK/doc/latest/nrf/samples/nrf9160/azure_iot_hub/README.html
From this guide it is explained how to provision the nrf9160-dk to Azure IoT Hub: https://developer.nordicsemi.com/nRF_Connect_SDK/doc/latest/nrf/include/net/azure_iot_hub.html
First I tried to create my own self-signed certificates with this tool: https://github.com/Azure/azure-iot-sdk-c/blob/master/tools/CACertificates/CACertificateOverview.md
I can upload the certificates to Azure and I can get them verified 
I have then created a new device called nrf9160 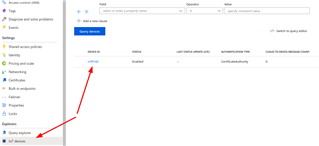
As part of the certificate creator tool (https://github.com/Azure/azure-iot-sdk-c/blob/master/tools/CACertificates/CACertificateOverview.md) I also make a "leaf" device where I type in the device name (nrf9160). This creates private key and device certificate. This is uploaded to the nrf9160-dk 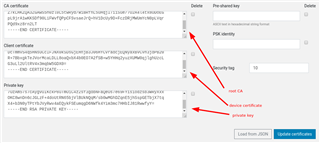
The security tag is set to 10.
I then configure my prj.conf file