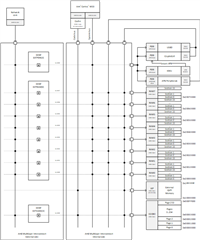
When evulating the nrf5340 for one of our projects, two questions came up regarding some of the security features used to mitigate tampering and malicious code:
- What is the state of the debug port on reset? Is there a window of time before the APPROTECT fuse is used by the hardware to disable the port and reset were the port might be accessible?
- For the DCNF that blocks the network core from reaching the app domain, are those registers only accessible from the network domain? Is there a way for the app core to block traffic from the network domain?