Dear All,
Hardware :
-
nrf52840 dongle
-
firmware : 3.1.0
Software:
-
wireshark 2.6.8
-
python : 3.7.3
-
pyserial : 3.5
-
Jlink : 6.88a
-
OS : debian buster 10
-
kernel : 4.19.0-12-amd64
I have installed all the software successfully without fail :
nrf sniffer install :
./nrf_sniffer_ble.sh --extcap-interfaces
extcap {version=3.1.0}{display=nRF Sniffer for Bluetooth LE}{help=www.nordicsemi.com/.../nRF-Sniffer-for-Bluetooth-LE}
control {number=0}{type=selector}{display=Device}{tooltip=Device list}
control {number=1}{type=string}{display=Passkey / OOB key}{tooltip=6 digit temporary key or 16 byte Out-of-band (OOB) key in hexadecimal starting with '0x', big endian format. If the entered key is shorter than 16 bytes, it will be zero-padded in front'}{validation=\b^(([0-9]{6})|(0x[0-9a-fA-F]{1,32}))$\b}
control {number=2}{type=string}{display=Adv Hop}{default=37,38,39}{tooltip=Advertising channel hop sequence. Change the order in which the siffer switches advertising channels. Valid channels are 37, 38 and 39 separated by comma.}{validation=^\s*((37|38|39)\s*,\s*){0,2}(37|38|39){1}\s*$}{required=true}
control {number=3}{type=button}{role=help}{display=Help}{tooltip=Access user guide (launches browser)}
control {number=4}{type=button}{role=restore}{display=Defaults}{tooltip=Resets the user interface and clears the log file}
control {number=5}{type=button}{role=logger}{display=Log}{tooltip=Log per interface}
value {control=0}{value= }{display=All advertising devices}{default=true}
wireshark :
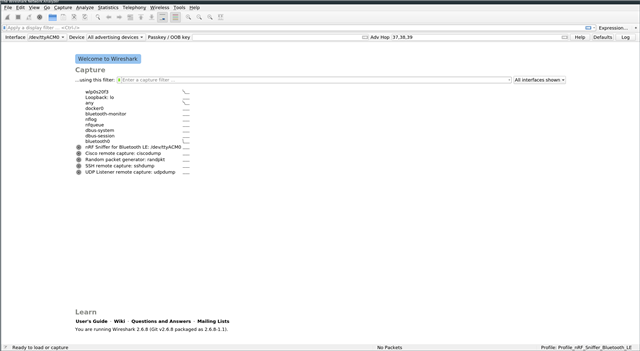
The green LED on the dongle starts blinking.
I am transmitting ble packet from anther nrf board.
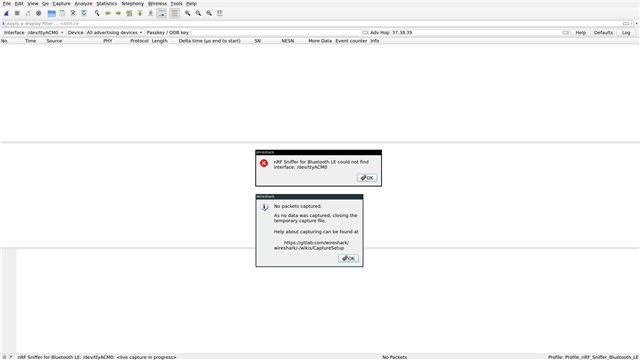
Unfortunately, wireshark is not capturing any packet. When I stop the capture I get this message :
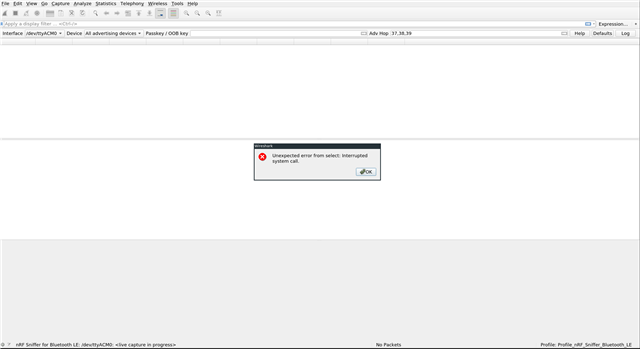
Any ideas would be greatly appreciated.
Fethi FEZAI