Hi,
I am evaluating nRF5340 for using it in a smart lock product with high security. I had evaluated nRF52840 before this
and was impressed with the integration that the crypto apis have the cryptocell-310 for BLE related link layer security
like LESC in 4.2.
In 5340 I believe the cryptocell-312 resides only the application domain, which is mentioned in the link below
https://blog.nordicsemi.com/getconnected/why-does-the-nrf5340-have-two-cores
Although a reply to a comment mentions that the network processor has its own hardware for over the air encryption
is this the hardware AES block or is this some how connected to the cryptocell-312 through the AHB bus like shown below?
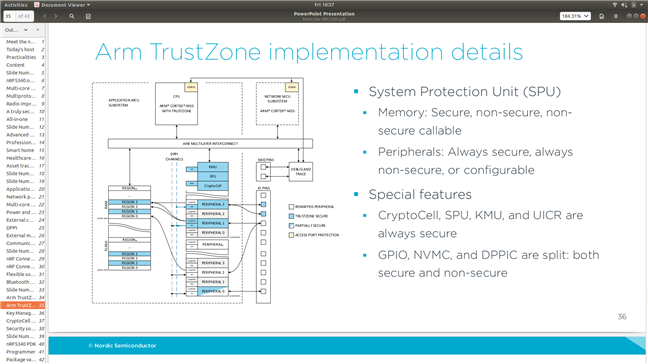
Also for LESC pairing where the stack needs to perform ECDH key exchange is this done in the cryptocell-312 or done via
software crypto backend?
In case the application need to do peer authorization, verification or nounce hashing etc using the cryptocell-312 ECDSA, SHA256
or any of the crptocell-312 algorithms can this code reside in the network processor and still use the cryptocell across the AHB bus?
This is so that the custom application handshake can reside close to the BLE stack (for e.g if OOB pairing needs the secret to be fetched
from the KMU). IPC between the two cores would make this possible I believe but its still an overhead in design and complexity.
What I envision is that all application validation and authorization, session keys etc be handled as a small and simple application in
the network processor with access to the cryptocell-312 and all business logic reside in the application processor.
So is the crypto hardware (CC312 ) backend apis available to the network processor via AHB?


