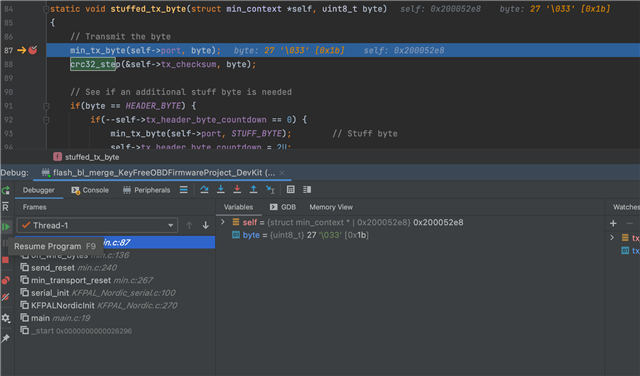
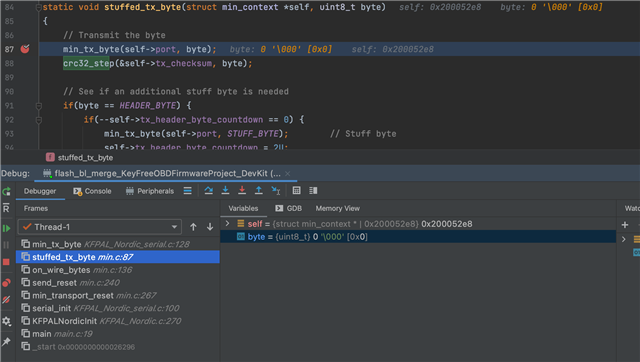
I've got an issue where calling a function is overwriting a variable in the calling function. See attached screenshots. In the first, byte is 0x1b. After stepping into the function (without any more code being executed) byte is overwritten with 0x0. I don't know where to start to debug this issue! Fortunately it is easily reproducible (in my firmware), and happens every time. Any suggestions? I'm using GNU Arm Embedded Toolchain 10-2020-q4-major, debugging here with arm-none-eabi-gdb in CLion. Stepping over instructions I can see the corruption occurs during the bl instruction:
0x0004f492 <+6>: ldrb.w r0, [r0, #512] ; 0x200 => 0x0004f496 <+10>: bl 0x28b64 <min_tx_byte> // stepi triggers corruption
However, this doesn't occur every time this function is called, only during a few specific calls. The calling function is in a linked library, and the called function is in my main application, not sure if that makes any difference but explains the large delta in the bl instruction. I've checked the softdevice ram allocation (it requested 0x3120 bytes, so RAM size is 0xcee0, and I've defined __HEAP_SIZE=0 __STACK_SIZE=0x2000).