Hi,
How does numeric comparison works? Shouldn't both devices share parameters in order to display the same number? How can we be protected from MITM?
Thanks!
Hi,
How does numeric comparison works? Shouldn't both devices share parameters in order to display the same number? How can we be protected from MITM?
Thanks!
Hi,
function g2 includes both public keys. In case of MITM attack, one side will have PK(Alice)+PK(Eve), other side - PK(Eve)+PK(Bob), numbers will never match.
Hi,
function g2 includes both public keys. In case of MITM attack, one side will have PK(Alice)+PK(Eve), other side - PK(Eve)+PK(Bob), numbers will never match.
Ok,
So the random number is generated from diffie-hellman key?
g2 uses both public keys and exchanged random numbers, not an ECDH secret:
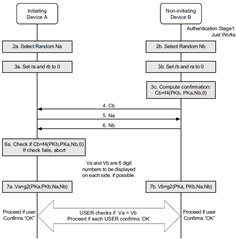
Thanks!
One more question - I assume the basic diffie-hellman (modulu functions) and elliptic curve diffie hellman work differently, but the idea of using public and private key and generating shared secret it the same, right?