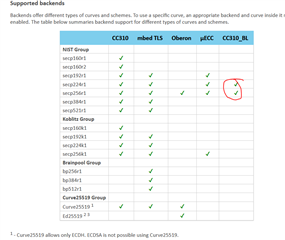
Hi, all
I tested nRF5_SDK_17.0 crypto library example with nRF52840, and compile information:
1>test crypto ECDH and ECDSA with enable CC310 :
==============================================================================
Total RO Size (Code + RO Data) 59692 ( 58.29kB)
Total RW Size (RW Data + ZI Data) 36072 ( 35.23kB)
Total ROM Size (Code + RO Data + RW Data) 59852 ( 58.45kB)
==============================================================================
2>and remove crypto test but keep print log:
==============================================================================
Total RO Size (Code + RO Data) 24976 ( 24.39kB)
Total RW Size (RW Data + ZI Data) 39888 ( 38.95kB)
Total ROM Size (Code + RO Data + RW Data) 25120 ( 24.53kB)
==============================================================================
you can see CC310 crypto consume about 34K flash, that's too big to us
in my opinion, crypto library just some control code for register and the compute is implemented with hardware.
is there any misunderstand, and method?