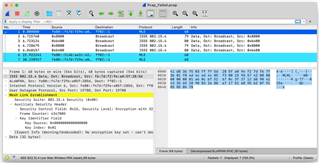
I have developed a python script to sniff the OpenThread network using the Nrf802154Sniffer() library, which generates a pcap file.
I used it with the nRF Sniffer hardware (nRF52840 DK and nRF52840 Dongle).
The problem is that in the pcap file generated, I found that there are packets that are not well analyzed, but in Wireshark it sniffs packets well.
Do you have any idea where this problem comes from.
thank you in advance
Best regards,
Ayoub GH