Hi ,
i am using nrf52840 dk board. and using 17.1 sdk for examples code.
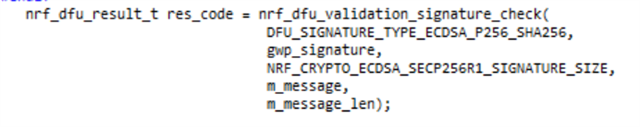
i am trying to customize open bootloader code and trying to validate the signature of a input data by using nrf_dfu_validation_signature_check() API.
Note: - i am having my own public and signature data, which i fed to this function.
But i am getting "NRF_DFU_RES_CODE_INVALID_OBJECT" in return from the above API.
Below i attcahed the calling function with input parameters.
static uint8_t m_message[] = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789";
const size_t m_message_len = 36; // Skipping null termination
Regards


