Hi Community,
I am using ble_hrs_heart_rate_measurement_send API to send notifications to my central device which is a android mobile.
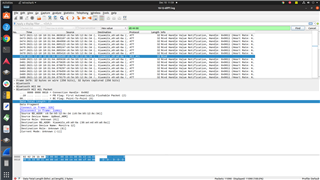
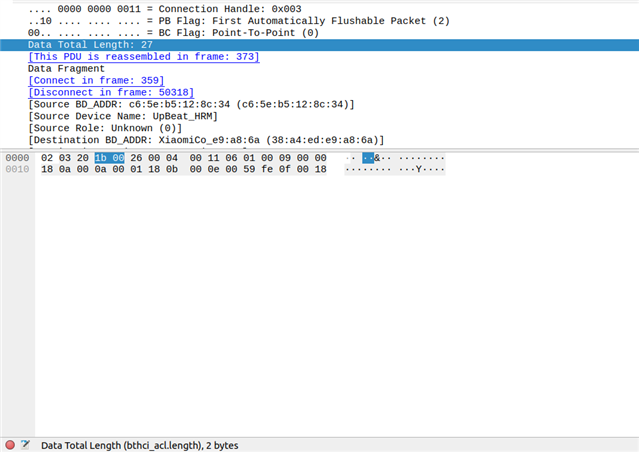
Recently I have observed packet loss at central device due to L2CAP packet length is differ from ACL packet length.
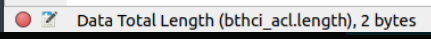
In the HCI_ACL packet, total length is 27. But in the ACL payload which is L2CAP packet length is showing as only 2. Total payload is present in L2CAP.
Hence my application running on mobile is unable to fetch the packet from L2CAP since it is dropped at HCI.
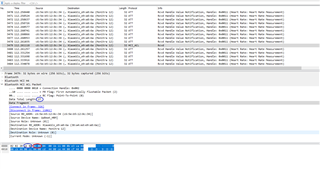
Attached is wireshark screen shot for reference. Highlighted packet was dropped at HCI.
Where could be the issue ? Any pointers would be really helpful.
Best
Lakshmikanth