Hi Nordic team
Customer Delta was running a street lamp project.
For AWS FOTA, they applied a AWS account and firmware update already can work.
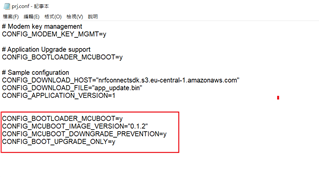
However, it looks like no version control ability. No matter new or old firmware from AWS,
NRF9160 accepted both.
How can we make it at NRF9160 side? Let NRF9160 reject older version update.
This project was from SDK Connect v1.3.0 http_application_update.
Jeffery