Hey! I'm trying to sniff the data moving between a Bluetooth LE button and a Central.
Installation of the Bluetooth LE Sniffer went pretty smoothly but Wireshark only shows `ADV_IND` packets.
- nRF52840 DK
- macOS Intel on Catalina
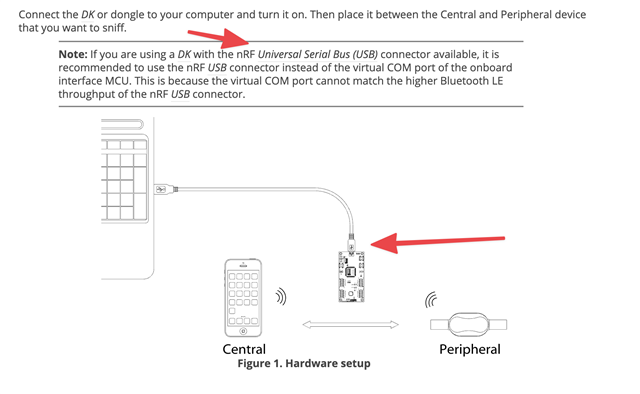
- I have to use a USB-C hub to go from the DK to the MacBook Pro
- Wireshark Version 3.6.1 (v3.6.1-0-ga0a473c7c1ba)
- JLink version 7.60d
- nRF Bluetooth sniffer v4.1.0
What can I do to see all the packets going between the the button and the central?