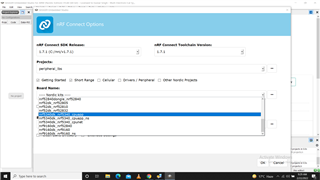
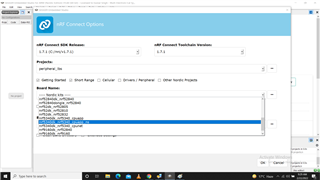
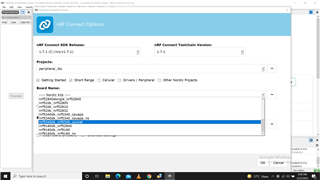
Hi, I want to know brief aboout difference and objective of different types of Zephyr projects. When using nRF Connect SDK, in SES a project is created, 3 options are available as shown in attached images. For me there are variuos options and combinations :
1. Project with cpuapp only
2. Project with cpuapp_ns only
3. Project with cpu_net ony
4. Project with cpuapp and cpuapp_ns in a single solution
5. Project wth cpuapp and cpu_net
6. Project with cpuapp_ns and cpu_net
7. Project with cpu_ns and cpu_net
8. Project with cpuapp, cpuapp_ns and cpu_net
Please, may some one explain, in what case which combination is prefered and how to create mixed project like options 4 to 8.
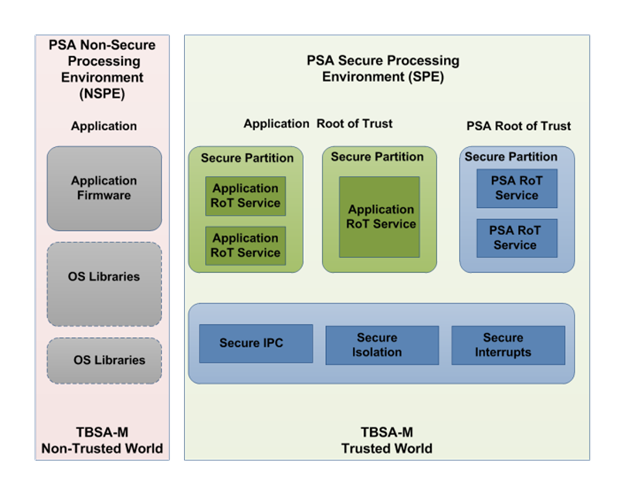
What difference berween cpuapp and cpu_ns ?? Is cpuapp secure type by default ?