Hoping someone can help.
I am using an nRF52840 MDK USB dongle running nrf firmware in wireshark / nrf sniffer. I am attempting to sniff the bluetooth messages from my pool controller, so that i can then add the commands to an espcontroller (then add it into my home automation).
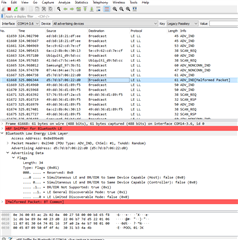
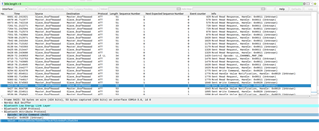
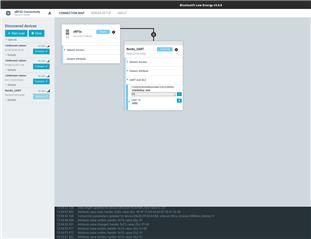
I am able so see and select the nrf sniffer for Bluetooth LE interface in the list in wireshark, then once selected, I can see the bluetooth pool controller in the list of devices in Wireshark.
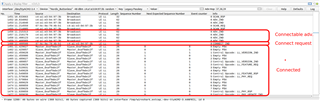
I am able to see constantly updating SCAN_RSP, SCAN_SEQ and ADV_IND records in the list, while my iphone is NOT connected to the pool controller, but then once I connect to the bluetooth controller from my iPhone, the messages stop and I get a final message ADV_EXT_IND [malformed Packet]. Once i disconnect my phone from the pool controller, the messages start coming through again.
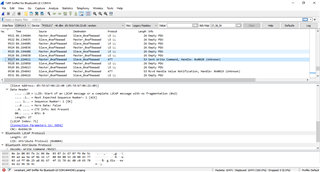
If i open one of the messages, I can see a value stating Simultaneous LE and BR/EDR to Same Device Capable (Host): false, and another stating Simultaneous LE and BR/EDR to Same Device Capable (Controller): false so i suspect i cannot connect multiple bluetooth devices to the controller.
Is there a way to get around this to sniff the messages as i click buttons?
thanks in advance for your assistance