Hi there,
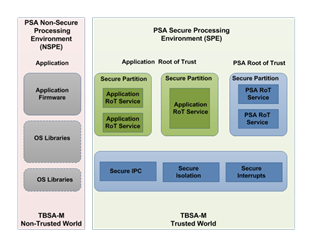
According to our understanding, on CPU reset the entire core is set to the secure except for non-secure peripherals. Is this understanding correct?
We are trying to figure out why one would want to use non-secure regions at all, instead of just running the entire application as secure, which is the default at CPU reset above. Is it possible to provide is with some simple use cases just so that we can better understand this?
Kind regards,
Frikkie