Hi all,
I'm a beginning hobbyist with nRF52. I'm programming a BC805m using my nRF52-dk and nRF Connect SDK v1.9.0 (zephyr & Segger Embedded Studio).
The learning curve was quite steep, but I'm 99% done with my project. There is one issue remaining.
My project is a key fob to turn on an e-bike over BLE. There are three commands: A) turn bike on, B) turn bike off, C) toggle lights. These use two different GATT services. A+B are done by sending a single byte via a device specific GATT service. C is via the standard UART over BLE GATT service.
On the DK (even in 52805 mode) everything is working great.
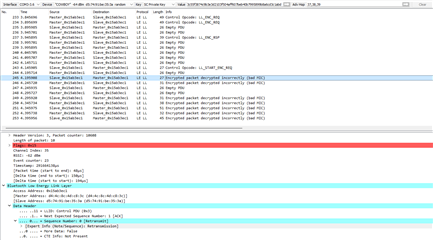
On the external module, A and B work great. C does nothing. There is no error. This is the code snippet that I'm using (the exact same code and config are working the nrf52-dk in both 52805 and 52832 mode).
static void function toggleLights() {
uint8_t d[] = {0x0A, 0x10, 0x00, 0x01, 0x00, 0x01, 0x02, 0x00, 0x00, 0xd4, 0xb1}; // off
bt_gatt_write_without_response(default_conn, 0x38, d, 11, false);
}
The only configuration change I had to make for the external module to work was to use CLOCK_CONTROL_NRF_K32SRC_RC as there is no external crystal attached to the BC805m.
Can someone point me in the right direction to start debugging this? Let me know if you need more information.
Edit 1: Via the debugger I've confirmed that the handle (0x38) is the same on the BC805m module.
Edit 2: For reference, this is the function that does work on both modules.
static void bike_turn_off() {
uint8_t d[] = {0};
bt_gatt_write_without_response(default_conn, 0x19, d, 1, false);
}
Thank you!
Jouke